Whether you're considering New Relic or you're already using our capabilities, this glossary of common terminology can help. And if you're looking to get started, see Get started with New Relic.
A New Relic organization can have one or more accounts. An account can be considered a workspace: a space to monitor or analyze data relating to a specific project or a specific team. Each account has its own account ID, and that ID is used for some account-specific tasks, like making API calls. For more on why you'd create an account, see Account structure.
The word "account" is sometimes used in a more general industry sense. For example, it is sometimes used to refer to a New Relic organization, or a New Relic customer, or to a New Relic user's user record. In technical terms, though, at New Relic an account refers to an account with an account ID.
A New Relic organization can have one or more accounts.
An "account family" refers to a parent account and the children accounts under it: in other words, a group of related accounts tied together by billing.
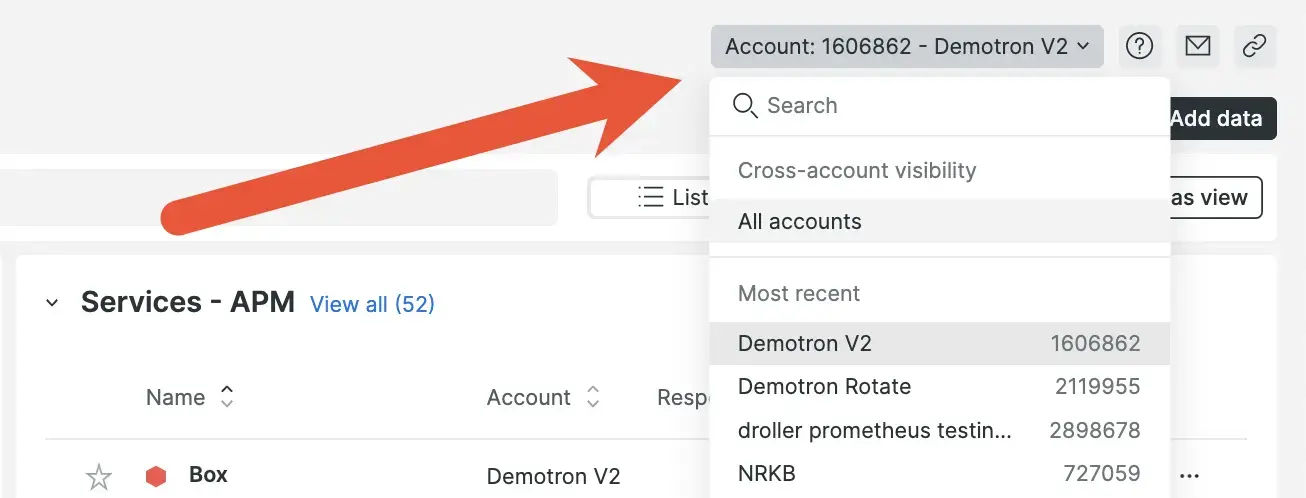
If you have access to more than one account in a multi-account organization, you can use the account switcher to switch between accounts. It's located in the top right of the New Relic home page and some other entity list views.
For more on factors that affect access to accounts, see Factors affecting access.
To find account settings, use the user menu.
A New Relic agent is an installable piece of software that integrates with multiple types of technologies (for example, web frameworks, operating systems, and types of databases) and reports data to New Relic, usually on a specific cadence. We have agents, an infrastructure agent, a agent, and mobile monitoring agents. The various technologies that our agents integrate with are just some of our many integrations.
For more information, see:
For our alerting feature, this refers to the length of time in seconds to wait for the aggregation window to fill with data. Required when using aggregation_method types CADENCE or EVENT_FLOW.
In the context of NRQL alerts, you can use NRQL functions, such as sum(), average(), or latest() to choose how the data points in an aggregation window should be processed into a single data point. The single aggregated data point is what's passed through the alert evaluation process.
In the context of New Relic alerts, we aggregate data into windows, and needs to determine when the current window ends and the next one begins. The aggregation_method is the logic that tells us when we have all the data for a given aggregation window. Once the window is closed, the data is aggregated into a single point and evaluated against the threshold. This field is optional. One of the following three values can be specified:
EVENT_FLOW: (Default) Each aggregation window will wait until it starts to see timestamps arrive that are past its own delay setting. Once this occurs, the data is published. Relies on the timestamps of arriving data, so wall-clock time is no longer relevant. Works best for sources that come in frequently and with low event spread (high througput metrics)CADENCE: Classic New Relic logic where each evaluation window waits exactly as long as theaggregation_delaysetting, using the wall-clock time as a timer.aggregation_delayis required when using this option. Data arriving too late will be dropped, which can cause false alerts.EVENT_TIMER: Each aggregation window has a timer on it, set to theaggregation_timersetting. The timer starts running as soon as the first data point appears for that aggregation window (based on the data point's timestamp). Theaggregation_timeris reset for each new data point that arrives for that window. Once theaggregation_timerreaches 0, the aggregation window is published. Ideal for sparse and batched data, such as cloud integrations and infrequent error logs.
In the context of New Relic alerts, this is the length of time in seconds to wait after each data point is received, to ensure the entire batch is processed. Required when using EVENT_TIMER aggregation_method type.
In the context of New Relic , streaming alerts gathers data together into specific amounts of time. These windows of time are customizable.
Data points are collected together based their timestamps and reported as a batch. The customizable aggregation window provides greater flexibility and fewer false alert events when alerting on irregular or less frequent data points.
AI, or artificial intelligence, refers to computer systems that can understand, learn, and perform tasks that normally require human intelligence. At New Relic, when we say AI, we mean the layer of your environment that uses a large language model (LLM) to generate a response (or make a decision) based on end-user prompts.
An alert communicates an event or alert event that designated personnel can track through alerts.
For an explanation of how basic alerts concepts are related, see Concepts and workflow.
An alert condition (or condition), identified by its unique numeric condition_id, contains the criteria for creating an alert event. The condition includes the threshold that is set for a metric timeslice or a custom metric over time on a chosen target.
For an explanation of how a condition relates to other basic alerts concepts, see Concepts and workflow.
In the context of alerts, streaming data is assessed on a set of aggregation windows to determine if an alert condition is breaching or recovering.
The aggregation window time is how long we'll collect data before running the NRQL query condition. The offset evaluation time is how long you want us to wait for late data before assessing it.
If a window doesn't have any data points, it's treated as a gap for loss of signal.
In the context of alerts, an alert policy is a collection of one or more alert conditions, one or more notification channels, and an Alert event preference setting.
A condition contained within a policy may open an alert event depending on the alert event preference settings. In this case, all channels attached to the policy will generate notifications.
For an explanation of how a policy relates to other basic alerts concepts, see Concepts and workflow.
When a service or application behaves abnormally, New Relic's alerting features flag it as an anomaly. You can find anomalies in the activity feeds throughout New Relic. You can also create custom configurations to get notifications or track anomalies in other types of entities, like hosts and mobile apps.
For more information, see [anomaly detection] (/docs/alerts-applied-intelligence/applied-intelligence/proactive-detection/proactive-detection-applied-intelligence/)
Apdex is an industry-standard way to measure users' satisfaction with the response time of an application or service. New Relic rates each response as Satisfied, Tolerated, or Frustrated, and uses these ratings to calculate an overall user satisfaction score.
For more information, see Apdex: Measure user satisfaction.
The response time above which a transaction are rated frustrating. Defaults to four times apdex_t.
Requests that complete in less than
apdex_tare rated satisfied.Requests that take longer than
apdex_t, but less than four timesapdex_t(apdex_f), are tolerated.Any requests that take longer than
apdex_fare rated frustrating.For more information, see Apdex: Measure user satisfaction.
The response time above which a transaction is considered tolerable. The default value is 0.5 seconds, but you can change this in your Apdex settings.
Requests that complete in less than
apdex_tare rated satisfied.Requests that take more than
apdex_t, but less thanapdex_f, are tolerated.Any requests that take longer than
apdex_fare rated frustrating.For more information, see Apdex: Measure user satisfaction.
New Relic offers a variety of APIs and SDKs. For more information, see the introduction to New Relic APIs.
New Relic APM (application performance monitoring) provides monitoring of your web or non-web application's performance. supports apps using several programming languages.
For New Relic purposes, any program instrumented by New Relic.
Some New Relic solutions assign a monitored application a unique application ID, often shortened to app ID. When present, this ID is available in the UI. It is also reported as an attribute and can be queried.
For how to determine this, see Find app ID.
The name that New Relic combines with your to uniquely identify a particular app. For more information, see Name your application.
Attributes are key-value pairs attached to data objects reported to New Relic. Attributes add detail, and they're similar to tags or labels in other SaaS software. You can explore this data by querying or searching via the UI or by using the data dictionary.
Examples:
APM reports a
Transactionevent. This includes timing data for the transaction in adurationattribute, which might have a value of.002.Our infrastructure monitoring reports a
ProcessSampleevent. This includes a variety of CPU usage attributes, including acpuSystemPercentattribute, which might have a value of.01.Our Telemetry SDK reports a
Metricdata type for storing metrics, with attached attributes likemetricNameandnewrelic.source.Some New Relic tools allow you to report custom attributes to enhance your monitoring.
For more information about attributes in APM, see Agent attributes.
For our end-user browser monitoring solution, see Browser Monitoring.
For information on what browsers support New Relic, see Supported browsers.
Measures the speed and performance of your end users as they navigate to your site from different web browsers, devices, operating systems, and networks. For more information, see Introduction to browser monitoring.
Refers to time spent in calls to external services from within the non-web transactions of a service. See web external.
See parent account.
New Relic offers cloud-based integrations with providers such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform.
The component that collects data from New Relic agents running on an app server, mobile device, or end-user browser. While the agent is installed on a user's app server, the collectors are centrally located in our data center.
In order to contact the collector, the agent must be able to reach New Relic domains and IP addresses. (The exact domain or IP depends on the New Relic monitoring tool.) The collector receives and interprets this data, and stores it in a database. The data is then retrieved and presented in the New Relic UI and by our various REST APIs.
Our command line interface (CLI) is a tool that lets you manage New Relic, including managing and controlling your use of New Relic at scale.
See alert condition.
Use alert conditions to define when and why your team will be notified if your entities aren't working the way you want. With conditions, you establish the criteria for notifications about lag time, code errors, Apdex scores, high CPU usage, and more.
For more information, see alert events.
A container is a standard unit of software that carries all the necessary pieces of code and all of its dependencies in order for your application to run smoothly across a variety of computing environments.
The number of calls your application receives each minute. This usually corresponds to the number of page views or external connections, and is usually the same as RPM (requests per minute).
The time consumed by code minus the wait time for a transaction. This is the time actually spent processing the transaction. It appears in the New Relic UI at the top of the transaction view for the agents that provide it (Ruby and PHP only).
A key-value pair added to a transaction or event in order to gain additional information about it. For more information, see custom attributes.
A customizable dashboard with charts and tables that includes data from multiple New Relic data sources. For more information, see dashboards.
An event, in New Relic terms, is a data object with attached attributes. New Relic reports default event types, like Transaction and TransactionError. You can also create your own events. Events can be queried, and are used in some other features.
You can generate custom events with APM agents, the browser monitoring agent, the mobile monitoring agents, and via the Event API. Alternatively, you can add custom attributes to some existing default New Relic events.
Custom instrumentation allows you to extend New Relic monitoring to instrument code elements New Relic doesn't automatically instrument. Custom instrumentation is useful when your framework is not supported by New Relic, or when New Relic fails to pick up some element of your program. You can also use custom instrumentation to block a transaction from being reported entirely. For more information, see Custom instrumentation.
Metric timeslice data that is manually recorded via an API call. Custom metrics allow you to record arbitrary metrics; for example, timing or computer resource data. All custom metric names must be prefixed with Custom/. For more information, see Custom metrics.
Not to be confused with custom instrumentation data.
See collector.
In the Metrics and events UI, you can access, query and customize your data, create visualizations, and make connections between your services in a consistent and curated experience.
For more on this, see Introduction to metrics and events.
In the context of alerting, when a data source enters a breaching state, a degradation period of time begins. The degradation period is set in the condition's threshold. An alert event will open if the source stays in a breaching state for the entire degradation period. In addition:
- If the data source enters a non-breaching state before the entire time has elapsed, the degradation period countdown is reset, and an alert event does not open.
- If your alert condition threshold is configured as
at least once in, the degradation period always lasts a single minute.
A dependency is the code that your application depends on in order to function. New Relic provides a list of all the applications, services, databases, and hosts we can tell are connected to an entity. On the Dependencies UI page, you can find an entity's upstream and downstream dependencies, and the paths to explore them.
In the context of alerting, destinations are where we send notifications about your data. A destination is a unique identifier for a third-party system that you use.
Destination settings contain the connection details to integrate with third-party systems and can be used across a variety of tools in New Relic.
A dimensional metric is a metric that has multiple attributes, also known as dimensions. At New Relic, we report dimensional metrics using the Metric data type. For more on other metric data types, see Metric data.
Distributed tracing is a method of monitoring requests as they flow through various cloud environments. Distributed tracing tracks a request by tagging it with a unique identifier. This allows your team to have a real-time understanding of the interactions taking place within your entities.
An open platform for distributed applications, which allows you to assemble multi-container portable apps. Infrastructure monitoring includes integrated Docker monitoring. For more on Docker, see the Docker website.
The period of time when customers cannot access your site and your app is not reporting to New Relic. For more information, see Synthetic monitoring and Types of synthetic monitors.
In New Relic, an entity is anything we can identify that has data you can monitor. An entity can be something you monitor directly, like applications and microservices, or indirectly, like data centers.
For more on this, see What are entities?
In the software industry, events can be thought of as simply “things that occur in a system.” For example, changing a server setting is an event. Another example: a website user clicking a mouse.
Some events generate a stored record, and that record is typically also called an event. To learn how New Relic uses events, see New Relic data types.
An expected error is a common error that you don't want to affect your Apdex score or error rate. For more information, see Manage errors in APM.
An external service is a service that is out-of-process relative to a service that is instrumented and reporting data to New Relic. An external service calls or is called by that instrumented service.
In most places in the New Relic UI, external services are uninstrumented services that do not report telemetry themselves to New Relic, but are observed from the outside using the data that instrumented services report about incoming or outgoing calls. For example, an external service named api.stripe.com is not instrumented and reporting data to New Relic itself, but is known to New Relic when a service instrumented with the New Relic agent makes an HTTP request to the hostname api.stripe.com.
A facet helps your team compare information that has many variables. You can query New Relic data in NRQL and use facets to segment the displayed data. For example, if you want to know where your CPU data is being used, you can segment your CPU data by the hostname facet:
SELECT average(cpuPercent) FROM SystemSample FACET hostname
New Relic Flex is an application-agnostic, all-in-one infrastructure integration. With it, you can build your own integration that collects metric data from a wide variety of services, and that can instrument any app that exposes metrics over a standard protocol (HTTP, file, shell) in a standard format (for example, JSON or plain text) to the terminal.
It's a recommended way to create a custom integration, because it doesn't require coding skills.
A framework is a structured collection of pre-defined functions, into which an application builder inserts their own code to build their application. A framework is not the same as a library. While a library is a collection of functions you can call as needed, a framework is a skeleton for your application. The functions in that framework then call your functions. For more about the distinction between a framework and a library, see What is the difference between a framework and a library?.
New Relic automatically instruments many common frameworks. For more about the frameworks New Relic supports, browse our solutions on Instant Observability.
The most important metrics for a given entity, use case, or technology. Golden metrics can include golden signals: latency, traffic, errors, and saturation.
Some New Relic UI pages have a health status indicator appearing next to an index of monitored entities. This is a colored bar (generally green, yellow, red, or gray) indicating the status of your app or other entity monitored by New Relic. It also indicates whether the entity has any alert policies assigned to it and whether there are any alert events.
Exceptions to the above-mentioned color palette:
- Learn about service map colors
- Our REST API (v2) uses
orangeinstead ofyellowfor the application's health and reporting status.
At New Relic, a host means one of the following:
- A physical machine is a hardware-based device with dedicated physical resources, including memory, processing, and storage. Each machine has its own OS which applications run on.
- A virtual machine (VM) is the software implementation of a physical machine that executes programs like a physical machine. One or more virtual machines can run on a physical machine. Each virtual machine has its own OS and allocated virtual machine resources such as RAM and CPU.
- A cloud instance is a type of virtual machine that is run in the public cloud. In this context, virtual machines and cloud instances are different from Java Virtual Machines (JVMs) and containers.
An error that you have told an APM agent not to report to the collector. For more information, see Manage errors in APM.
In the context of alerting, an alert event is generated when the conditions defined in an alert policy is exceed. An alert event record includes all of the open and close time stamps for each alert event, as well as chart snapshots of the data being evaluated around the time of each alert event.
You can view detailed information from the Alert events pages in the user interface. You can also select your preference for how we roll up alert events.
For an explanation of how an alert event relates to other basic alerts concepts, see Concepts and workflow.
Infinite Tracing is a fully managed distributed tracing service that observes 100% of your application traces, then provides actionable data so you can solve issues faster.
For more information, see /docs/understand-dependencies/distributed-tracing/get-started/how-new-relic-distributed-tracing-works.
By connecting changes in host performance to changes in your configuration, infrastructure monitoring provides real-time metrics and powerful analytics that reduce your mean-time-to-resolution (MTTR).
Infrastructure is specifically designed for complex environments that need flexible, dynamic server monitoring, from a physical data center to thousands of Amazon Elastic Compute Cloud (Amazon EC2) instances and other types of integrations.
Insights was the name for the New Relic product that previously governed the reporting of custom events, and the ability to query and chart your New Relic data. These features are now a fundamental part of our platform and are no longer governed by the Insights product or name. To learn more about these features:
Event API for reporting custom events
For historical reasons, the word "Insights" is still used in some places. For example:
For New Relic organizations on our original pricing model, Insights Pro is still the product name governing custom event data ingest and retention.
Some APM agents still have Insights language in their codebase. For example, the Java agent
custom_insights_eventsconfiguration.There is an API key called the Insights insert key.
Each instance identified by New Relic is assigned a unique instance ID. Instance IDs are most commonly found for JVMs (Java Virtual Machines), but can exist for each agent. This ID is used to uniquely identify it, and to retrieve data about that instance via the API. For more information, see the REST API's List instance IDs.
At New Relic, an integration refers to a connection between a technology and New Relic that allows the reporting of data to New Relic. So, for example, our agents contain various integrations (ways to report data from various app frameworks, or operating systems, or types of databases). Other integrations take the form of a configuration or a procedure (for example, changing a setting or an API endpoint) that allows a service (for example, AWS Lambda or PagerDuty) to send data to us.
In our mobile monitoring, an interaction is a specific code path initiated by a user interaction (usually a button press). An interaction is the mobile equivalent of a transaction, and like a transaction an interaction can be traced and monitored.
You can see much of the data included in an interaction in the BrowserInteraction event.
An interaction trace is a complete picture of a single interaction. With interaction traces, New Relic gives you much deeper visibility into a single slow interaction, which can help you understand a broader problem. Interaction traces are the mobile equivalent of a transaction trace. For more information, see Creating interactions (iOS) and Creating interactions (Android).
Inventory data is information about the status or configuration of a service or host. Examples of inventory data include:
Configuration settings
Name of the host the service is on
AWS region
Port being used
For more information, see Understand and use data.
In the context of alerting, an issue is a problem in your system that needs attention. An issue is made up of one or more alert events and anomalies we've correlated through machine learning or other means. You can receive notifications when issues are created, acknowledged, or closed.
For more information, see Alerts concepts & workflow.
In APM, a key transaction is a web transaction that the user has marked as particularly important; for example, key business events (such as signups or purchase confirmations), or transactions with a high performance impact (such as searches). Key transactions have their own pages in the UI and other customized values. For more information, see Key transactions.
Our log management and monitoring features give you the tools to collect, process, explore, visualize, and alert on your log data using your existing log forwarder. With all of your log data in one place, you'll be able to make better decisions, detect and resolve problems more quickly, and see your logs in context to troubleshoot faster.
Logs in context allows your log data to be seen in other New Relic platform experiences.
New Relic Lookout provides an intuitive view of entities that are deviating from normal behavior, using circle visualization. Color indicates severity, and size of circles conveys the scale of recent changes. You don't need to configure anything: New Relic Lookout automatically compares performance within the last five minutes against the previous hour.
See parent account.
In the software monitoring industry, a metric means a numeric measurement of an application or system. To learn how New Relic defines and uses metrics, see New Relic data types.
New Relic reports metrics in several ways. One variety of metric data is called metric timeslice data. For more about this type of data, see New Relic data types.
A metric grouping issue occurs when an account sends too many differently named metric timeslice data points to New Relic, and those individual web transactions are not properly aggregated. For example, rather than a single /user/controlpanel/ metric name, you might see /user/controlpanel/alice, /user/controlpanel/bob, and /user/controlpanel/carol. For more information, see Metric grouping issues.
The software that accepts synthetic monitor jobs from a private location. A minion is a packaged virtual appliance that runs in your hypervisor. For more information, see Private locations overview and install and configure private minions.
New Relic mobile monitoring allows you to monitor and manage the performance of your mobile apps on Android, iOS, tvOS, and other systems. Mobile monitoring provides end-to-end details, including crashes, throughput, HTTP requests, error traces, and more.
For our synthetic monitoring, a monitor ensures your website or API endpoint is available. For more information, see Adding and editing monitors.
At New Relic, we use namespaces to help organize the data we store in the New Relic database (NRDB). From a customer perspective, the most practically relevant use of the namespace concept is how it relates to data retention. The namespace is what sets the default data retention period for various types of data. For example, in a specific account, data in the Logging namespace all share the same retention, and data in the APM namespace all share the same retention.
New Relic Navigator makes it easy to explore large numbers of entities in one view. Navigator displays the entire estate of your system in a highly dense honeycomb view with traffic light colors based on alerts.
NerdGraph is our GraphQL API, an efficient and flexible query language that lets you request exactly the data you need, without over-fetching or under-fetching. NerdGraph calls get all the data you need in a single request. NerdGraph also makes it easier to evolve APIs over time and enables powerful developer tools.
You can use our NerdGraph API explorer to view the schema and find definitions. Take a look at our tutorial, or go right to the NerdGraph API explorer.
For more information, see Introduction to New Relic.
Our catalog is a collection of applications built on the New Relic platform. The catalog includes custom apps we've built, public open source apps, and any apps that you buid.
You can browse the catalog on New Relic.
NRQL is a query language, similar in form to SQL, that allows you to query the data stored in your New Relic account.
APM identifies transactions as either web or non-web. When New Relic does not detect a transaction was initiated by a web request, this is called a non-web transaction. For more information, see Background processes and other non-web transactions.
In the context of alerting, a notification is a message sent when an alert event opens, is acknowledged, or closes. The type of notification is defined by the alert policy's notification channel.
For an explanation of how notifications relate to other basic alerts concepts, see Concepts and workflow.
In the context of alerting, a notification channel is where we send a notification when an alert event opens, is acknowledged, or closes. Available channels include email, mobile push notifications, webhooks, and more.
In the context of our logging management feature, this is a security protocol that hides sensitive data in your logs through hashing or masking. After you've identified sensitive data you want to hide, you define it in the form of an expression. With that expression, you create an obfuscation rule that identifies instances of sensitive data in your logs, then automates masking or hashing, depending on the rule.
On-host integrations refer to integrations that reside on your own servers or hosts and that communicate with our infrastructure agent. For more information, see Introduction to on-host integrations.
At New Relic, "organization" can refer to one or more concepts:
- For New Relic account management purposes, a "New Relic organization" refers to all the assets and data belonging to a New Relic customer (for example, their accounts, their users, and their data). For more about this concept, see Organization and account structure.
- We sometimes use "organization" in a general way to refer to a business or non-profit entity.
With page load timing, New Relic monitors the full load time for end-user browsers. New Relic application agents dynamically inject JavaScript into the page, then capture the following key load points:
Navigation start: The user initiates the transaction.
First byte: The browser receives the requested page.
DOM ready: The browser has finished parsing DOM.
Page ready: Page loading is complete.
Page load timing is sometimes referred to as RUM, or real user monitoring. Unlike standard RUM, page load timing also captures JavaScript errors and AJAX requests. For more information, see Page load timing process.
Deprecated term; see attribute.
New Relic organizations can have a parent/child account structure and would be relevant for some features for organizations. The first account created in a New Relic organization is essentially the parent account: one impact of this is that that account is where the usage and billing data is reported to.
Learn more about account structure.
Parent accounts were previously referred to as master accounts, and child accounts were previously referred to as sub-accounts.
A unique URL that links to a view of New Relic at a specific point in time. Permalinks are useful for troubleshooting and for sharing interesting time windows with colleagues. On many New Relic UI pages, you can find the permalink icon at the top right of the UI. For more on this, see Platform basics.
As of May 2023, these links expire if they haven't been used in the past six months. Note the following about the six-month pruning routine:
- Since permalinks are not user specific, an older link you haven't used in six months may still be active if another user happens to make the same query.
- Links using the old long-form URL with Base64 never expire.
The component of New Relic that connects to your website to verify your website is accessible. New Relic has pingers in Europe, Asia, and the United States. Each pinger attempts to contact your website at least once every two minutes. If enough pingers are unable to reach your website, your application will be considered down.
For in-depth scriptable testing, including real browser tests and tests of API endpoints, see synthetic monitoring. Synthetic monitoring includes free ping monitoring, which allows you to monitor your website from locations around the world. For more information, see Types of synthetic monitors.
In the context of alerting, an alert policy is a bucket for similar alert conditions so that you can see them all in one place. So, if your team wants to examine all of the conditions for your Java application, you need to create a policy to contain those conditions.
For more information, see Alerts concepts and workflow.
Our Amazon integrations query your AWS services according to a polling interval, which varies depending on the integration. Each polling interval occurs for every AWS entity. For example, if you have thirteen Amazon elastic load balancers (ELB), each one will be polled every five minutes.
Depending on the AWS integration, there may be delays in the timing between the API request and the metric data returned. If you notice unusual delays, follow the integration troubleshooting procedures.
The number of pages per minute your application serves. This is usually used in the context of browser monitoring or mobile monitoring.
A synthetic monitor feature that allows you to run synthetic monitors from within your own systems by creating private minions. Private locations allow you to extend your synthetic coverage to new geographical locations, and to monitor websites behind your firewall such as an intranet site. For more information, see Private locations overview.
At New Relic, quickstart refers to all methods of installation needed to get you one or both of the following:
Additional (in addition to our curated dashboards) accessible from the Dashboards UI
Pre-built alerts
Quickstarts are featured on our Instant Observability pages: for example, this page includes a quickstart for .NET that gets you an extra dashboard and pre-built alerts in addition to what you would normally get by installing the .NET agent.
A recovery period of time begins when a data source enters a non-breaching state after being in a breaching state. The recovery period is set in the condition's threshold. An alert event will close when a source remains in a non-breaching state and the recovery period time has elapsed. If the data source enters a breaching state before the time has elapsed, the recovery period clock will reset and the alert event won't close.
Shorthand for regular expressions. A string of characters and operators that, when used in tandem with a programming language, searches a chunk of text for patterns. For example, if you wanted to locate any social security number in your logs, you could create a regex that searches your logs for a number pattern that follows a {3 digit-2 digit-4 digit} pattern.
The duration of time between a request for service and a response. These kinds of charts are used for our APM monitoring and browser monitoring. For more information, see Response time.
In the context of APM, this usually refers to using the same application name for multiple applications. This allows you to combine data in APM, either from multiple applications, or from multiple instances of an application. For more information, see Rolling up app data.
For distributed tracing, the root span is the first span in a trace. In many cases, the root span duration will represent the duration of the entire trace, or be very close to it.
However, for more complex, modern systems that use a lot of asynchronous, non-blocking processes, this will not be true. For those systems, the root span's duration may be significantly less than the duration of the trace.
The term RPM usually refers to the number of requests per minute your application receives from users. This is usually the same as CPM (calls per minute).
Historically, some New Relic monitoring solutions, like and browser monitoring, used to contain RPM in the URL; for example, https://rpm.newrelic.com. This language use originally referred to Rails performance management because the first iteration of New Relic monitored Ruby on Rails applications. We monitor many more languages and systems than just Ruby now.
See browser monitoring.
In the context of alerting, a runbook contains standard procedures and operations typically used by system administrators, network operations staff, and other personnel to handle outages, alert alert events, and other situations. If your organization stores runbook instructions as URLs, you can link this information to an alerts policy so your personnel has easy access to this information when an alert event breaches the defined policy thresholds.
SAML is an XML-based data format for sharing authentication data between two parties. For information about our SAML features, see SAML SSO.
Selenium is an open-source browser testing suite. Synthetic monitoring uses Selenium to test monitored websites with real browsers. For more information, see monitor types.
A service is a cluster of runtime server processes that accomplish a particular task, usually service requests. Unlike an application, a service is not usually invoked by a human. Sometimes, though, "application" and "service" are used interchangeably.
We offer a large number of agents and integrations that allow you to report data from your services.
In the context of alerting, the signal is the stream of telemetry data that's watched and alerted on. You use a NRQL query to define a signal.
A unique signal is generated when the condition sees a unique stream of data that matches the NRQL query. Queries can contain a FACET clause in order for a single condition to generate multiple discrete signals; one for each matching facet. For more information, see NRQL alert conditions.
When we receive data and it's routed to the streaming alerts platform, your NRQL WHERE clause will filter the data coming in. The filtered streaming data is what's evaluated for loss of signal alert events, for example.
In a distributed trace, a span is a "named, timed operation representing a contiguous segment of work in that trace" (from OpenTracing.io definition).
For distributed tracing, spans are displayed in the distributed tracing UI, and the data type Span is available for querying.
See also root span.
SSL certificates encrypt data that is being transmitted. While New Relic refers to security certificates as SSL because it is a more commonly used term, all certificates adhere to industry standards for secure encryption in transit.
SSO (single sign on) allows you to manage user authentication in New Relic using an external SSO provider. For more information, see SAML SSO.
In the context of alerting, this is what determines when the data in an aggregation window is processed. The streaming algorithm uses your server's clock time and the aggregation window size to trigger the alert evaluation process.
See master account.
Synthetic monitoring allows you to monitor your website or API endpoint via automated, scriptable tools. Use free ping monitor to ensure your website is accessible, or expand your monitoring with browser monitors, which test your website with real browsers. Go further with scripting, to script browsers or API monitors for sophisticated testing.
In the context of alerting, a target is a resource or component monitored by a New Relic monitoring tool that has been identified in an alert condition. When the data source for that target crosses the defined critical threshold, we open an alert event. Depending on your policy's alert event preference setting, alerts may create an alert event record and send notifications through the defined channels. See also entity.
Tags are key:value metadata added to monitored apps, hosts, dashboards, and other entities to help you organize your data and make it easier to use. For details, see Tags.
When you're using New Relic, you're gathering telemetry data. With New Relic, you monitor your systems and collect data in the form of metrics, events, logs, and traces. New Relic then stores that collected data in our servers, which you can access and analyze through your dashboards.
Thresholds are alert condition settings that define an alert event. Threshold values include the value a data source must pass to trigger an alert event and the time-related settings that define an alert event; for example:
Passing a certain value for at least x minutes
Passing a certain value only once in x minutes
While the data source passes a certain value, a degradation period starts. Likewise, when that data source stops passing a certain value, a recovery period starts. The durations of these two time periods are defined in the alert condition threshold settings.
Thresholds have a required critical (red) threshold and an optional warning (yellow) threshold. In the UI, the entity's health status indicator will change to yellow or red when a threshold has been crossed and an alert event will open.
For more information, see Define thresholds. For an explanation of how thresholds relate to other basic alerts concepts, see Concepts and workflow.
Throughput is a measurement of user activity for a monitored application. APM throughput and browser monitoring throughput are measured in different ways:
- APM: requests per minute (RPM)
- Browser: page views per minute (PPM)
A tier can refer to how New Relic categorizes or visualizes the various agent language ecosystems that we support. For example:
In APM, the color-coded categories that appear on your app's main Overview chart show response time spent in various functions, processes, or agents as tiers; for example, request queuing, garbage collection, Middleware, JVMs, etc.
In New Relic labels,
TIERcan be used to define or classify the client-server architecture; for example, frontend and backend tiers."Tier" may sometimes be used to refer to our pricing editions.
Typically, New Relic UI experiences show data for the past 30 minutes, ending at the current moment in time. To change the time window, you can use the time picker in the upper right section of the UI.
A time range can refer to a length of time selected in the New Relic UI. New Relic displays a time range depending on the range you select using the time picker.
A trace is a description of how a request travels through a system. Trace data helps you understand the performance of your system and diagnose problems. For more information on how we use trace data, see New Relic data types.
See health status.
A transaction is defined as one logical unit of work in an application. This term primarily refers to server-side transactions monitored by APM. For more information, see documentation about web transactions and non-web transactions.
The term transaction is also sometimes used in browser monitoring. In that case, it primarily refers to activity beginning with a browser-side web request and ending with a complete page load.
In New Relic APM, a transaction trace refers to a complete picture of a single transaction, down to the database queries and exact invocation patterns. With transaction traces, New Relic gives you much deeper visibility into a single slow transaction, which can help you understand a broader problem. For more information, see Transaction traces.
The New Relic user interface. For more information, see Standard page functions.
For details about New Relic users and how to manage them, see User management.
The user menu is in the bottom left of the New Relic platform and is where your organization- and account-related settings can be accessed. For more information, see Account settings.
Universal Time Coordinated (UTC), or Coordinated Universal Time, is a standard timestamp for synchronizing time around the world.
The numeric value obtained from metric timeslice data; for example, an average, minimum, maximum, total, sample size, etc.
This term has been replaced in the UI with alert event.
In the context of APM, web external describes the portion of time spent in web transactions communicating with external services from within the code of the service you're monitoring. That time can be a call to a third party (a payment provider, for example) or it could be a call to another microservice within your own company. Web external time demonstrates how performance is impacted by calls over a network to code executing outside the application you're measuring.
A transaction is defined as one logical unit of work in an application. This term primarily refers to server-side transactions monitored by APM.
Web transactions are initiated with an HTTP request. For most organizations, these represent customer-centric interactions and thus are the most important transactions to monitor. For more information, see Web transactions and Non-web transactions.
WebDriver is a Selenium component, used to control synthetic scripted browsers. Specifically, synthetic monitoring uses WebDriverJS, a Node.js-based flavor of Selenium. For more information, see Writing scripted browsers and Scripted browser examples.
Workflows are how you route alert notifications to the right people when problems occur. To make troubleshooting easier, you can add queries to workflows to automatically enrich your notifications with more info around the alert events.
For more information, see Workflows.
Workloads let you group entities that work together to provide a specific business value. Then you can easily monitor availability and resource consumption for what's relevant to you. For example, you could make a workload with all the hosts that make up a data center.
For more information, see Intro to workloads.