With our Active Directory integration, you can easily monitor the health of your directory services environment and proactively alert on potential issues.
Built with our infrastructure agent, the Active Directory integration gives you a set of pre-built and that let you view your most critical performance data, all in one place.
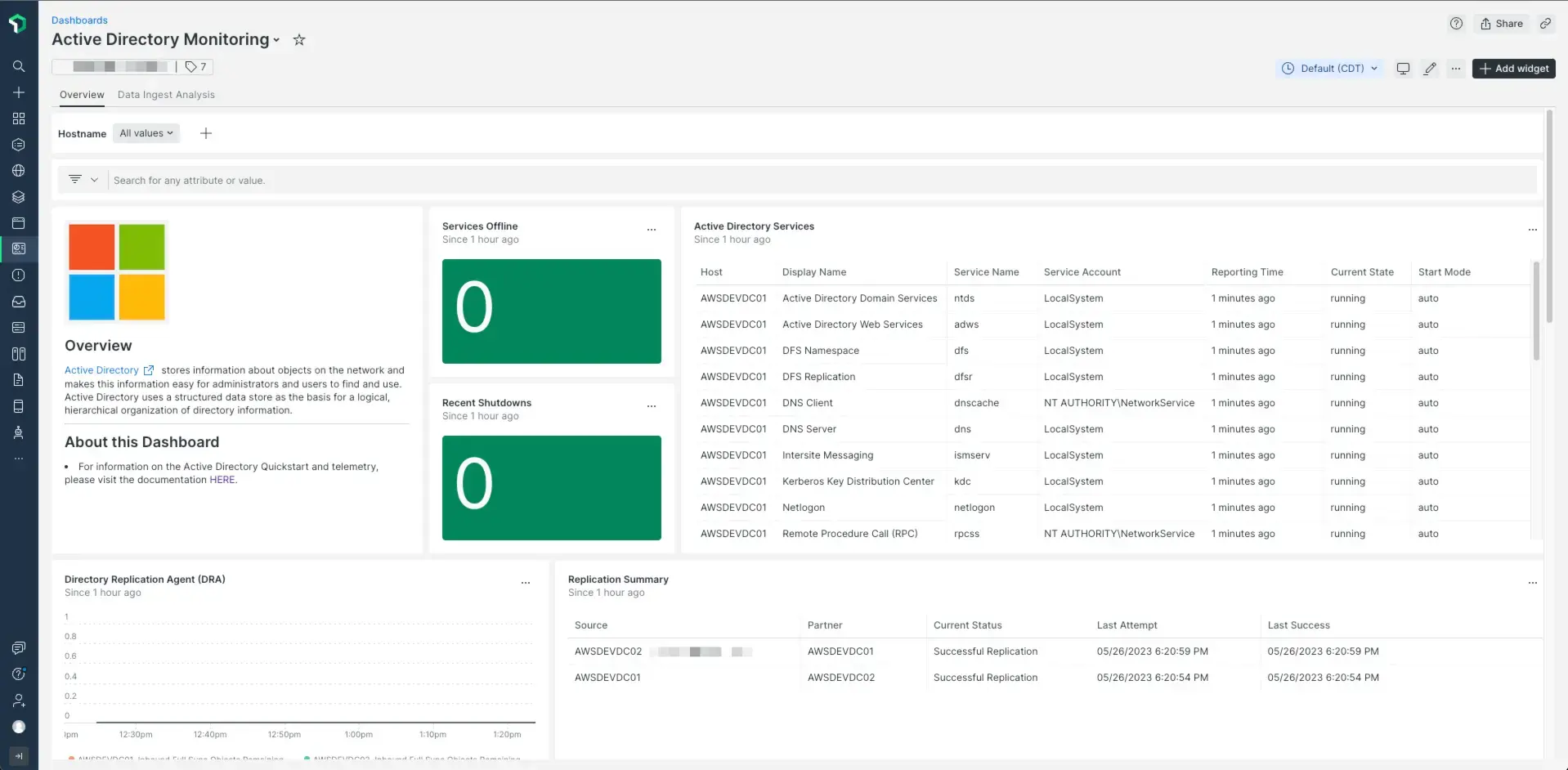
After setting up the Active Directory integration with New Relic, see your data in a dashboard like this, right out of the box.
To get the most out of this page, select the installation method that fits your environment. You need a New Relic account before starting the installation process.
Tip
Use guided install to quickly see your data in the UI
The guided install is a single CLI command you can run to monitor your Active Directory services. It's a good option for small organizations, or for anyone who wants to test out New Relic.
For a more permanent and scalable solution, we recommend the standard manual install of the integrations: keep reading for how to do that.
Install the infrastructure agent
To use the Active Directory integration, you need to first install the infrastructure agent on the same host. The infrastructure agent monitors the host itself, while the integration you'll install in the next step extends your monitoring with Active Directory-specific data.
Clone the Active Directory integration repo
Run the following command in your CLI to clone the New Relic Active Directory integration repository:
$git clone https://github.com/newrelic/newrelic-active-directory-integration.gitCopy configuration files
Copy the relevant configuration files from the repository to the agent, replacing $ROOT_PATH with the path where you cloned the repository:
# integrations.dCopy-Item -Path "$ROOT_PATH\newrelic-active-directory-integration\integrations.d\*" -Destination "C:\Program Files\New Relic\newrelic-infra\integrations.d" -Recurse
# logging.dCopy-Item -Path "$ROOT_PATH\newrelic-active-directory-integration\logging.d\*" -Destination "C:\Program Files\New Relic\newrelic-infra\logging.d" -RecurseInstall the integration
Install the Active Directory quickstart from the New Relic I/O catalog to add the relevant dashboard and alerts.
Find and use data
The collection of telemetry from Active Directory depends on various configuration and script files located in the infrastructure agent's directory structure like this:
C:\Program Files\New Relic\newrelic-infra\ ├── integrations.d │ ├── windows-active-directory-performance-counters.ps1 │ ├── windows-active-directory-performance-counters.yml │ ├── windows-active-directory-replication-checks.yml │ ├── windows-active-directory-replication-failures.ps1 │ ├── windows-active-directory-replication-partners.ps1 │ └── windows-active-directory-services.yml └── logging.d └── windows-active-directory.ymlEach of these files works together to present a full observability footprint. The resulting telemetry in New Relic consists of Metrics, Events, and Log data.
Event details
EVENT ATTRIBUTE | COUNTER NAME | DESCRIPTION |
|---|---|---|
|
| Number of connected address book client sessions |
|
| The number of objects remaining until the full synchronization is completed |
|
| The number of object property values received from inbound replication partners that are DNs that reference other objects |
|
| The number of object property values containing DNs sent to outbound replication partners |
|
| The number of directory synchronizations that are queued for this server but not yet processed |
|
| The number of directory reads per second |
|
| The number of directory writes per second |
|
| The number of pending update notifications that are queued but not yet transmitted to clients |
|
| The current number of threads that the directory service is using |
|
| The current number of threads that the LDAP subsytem of the local directory service uses |
|
| The time (in milliseconds) that is taken to complete the last LDAP bind |
|
| The number of currently connected LDAP client sessions |
|
| The rate at which LDAP clients perform search operations |
|
| The number of LDAP binds per second |
|
| The combined rate at which all processors on the computer are switched from one thread to another |
|
| The number of threads waiting to be executed in queue |
Windows Services
Collection of Active Directory Windows Services is accomplished via the native Windows Services integration using this configuration file:
windows-active-directory-services.ymlThe results of this collection are stored as dimensional metrics with the decorated label: label.primary_app = 'active_directory'.
Metric details
SERVICE NAME | DESCRIPTION |
|---|---|
| Active Directory Web Services |
| Distributed File System |
| DFS Replication |
| DNS Server |
| DNS Client |
| Intersite Messaging |
| Kerberos Key Distribution Center |
| Server |
| Workstation |
| Net logon |
| Active Directory Domain Services |
| Remote Procedure Call (RPC) |
| Security Accounts Manager |
| Windows Time |
Event details
EVENT NAME | ATTRIBUTE | DESCRIPTION |
|---|---|---|
|
| Integer indicating the total count of replication failures that have occurred on the specified domain controller. |
|
| String representation of the latest type of replication failure experienced by the specified domain controller. |
|
| Timestamp ( |
|
| Integer indicating the last error code received for a replication failure on the specified domain controller. |
|
| String name of the domain controller where the replication failure occurred. |
|
| Timestamp ( |
|
| Timestamp ( |
|
| Short name of the remote partner for replication. |
|
| Short name of the local server for |
Windows Event Logs
Collection of Active Directory Windows Events is performed with the integrated log forwarder on the infrastructure agent using this configuration file:
windows-active-directory.ymlThe results of this collection are stored as logs with the decorated label: logtype = 'active_directory'.
Log details
CHANNEL | EVENT ID | DESCRIPTION |
|---|---|---|
Security |
| Windows is shutting down |
Security |
| The system time was changed |
Security |
| An account failed to log on |
Security |
| A logon was attempted using explicit credentials |
Security |
| A replay attach was detected |
Security |
| An IPsec Main Mode security association was established |
Security |
| A service was installed in the system |
Security |
| Kerberos policy was changed |
Security |
| Encrypted data recovery policy was changed |
Security |
| System audit policy was changed |
Security |
| A user account was created |
Security |
| An attempt was made to change an account's password |
Security |
| An attempt was made to reset an accounts password |
Security |
| A user account was disabled |
Security |
| A user account was deleted |
Security |
| A user account was changed |
Security |
| Domain Policy was changed |
Security |
| A user account was locked out |
Security |
| A computer account was created |
System |
| The security descriptor version number could not be determined |
System |
| Security policies were propagated with warning. 0x534 : No mapping between account names and security IDs was done |
System |
| The attempt to establish a replication link for the following writable directory partition failed |
System |
| The Knowledge Consistency Checker (KCC) has detected problems with the following directory partition |
System |
| During the past [number] days; replication errors in one or more directory partitions have caused replication to be disabled for the specified naming context on the current domain controller |
System |
| Active Directory Domain Services has detected that the domain is still using the default password for the 'Administrator' account |
System |
| The session setup from the computer [computer name] failed to authenticate |
System |
| During the past [number] days; there have been a few replication errors in the forest. There may be network or connectivity problems in the forest |
Check the source code
This integration is open source software. That means you can browse its source code and send improvements, or create your own fork and build it.