Our automated user management allows you to import and configure your New Relic users and groups from your identity provider via SCIM. This guide provides OneLogin-specific details on how to configure the New Relic Login SCIM/SSO application.
Requirements
Before using this guide, read the automated user management requirements.
Note that these instructions require going back and forth between your identity provider and New Relic.
Step 1. Create authentication domain and enable SCIM
For how to get to the New Relic authentication domain UI, see Authentication domain UI.
If you don't already have one, create a new authentication domain for your SCIM-provisioned users by clicking + Add new.
For that authentication domain, under Source of users, select SCIM. Copy and save the API token for later use. Note that this will be shown only once.
Step 2. Set up OneLogin's New Relic app
Next, you'll be setting up OneLogin's New Relic SAML/SCIM app. To set this up:
- Go to the OneLogin web site and sign in with an account that has administrator permissions.
- From the OneLogin home page, click on Administration.
- From the OneLogin Administration page, choose the Applications menu.
- From the OneLogin Applications page, click on Add App.
- In the search field on the OneLogin Find Applications page, enter "New Relic by organization" (not "New Relic by account") and then click on the application when it shows in the search results.
- From the Add New Relic by Organization page, click on Save.
Step 3. Configure SCIM/SSO application
Configuration for the New Relic SCIM/SSO application is split across several forms. This section describes the different forms that need to be configured.
From the New Relic by organization application page, fill in the following forms:
Fill in the configuration form
In the left pane, select Configuration and complete the following:
- Get the authentication domain ID (top of New Relic's authentication domain UI and SCIM bearer token (in authentication domain UI as "SAML 2.0 endpoint) and input them into the appropriate fields in the OneLogin app.
- Leave the API Connection disabled until all the configuration described in the following sections is completed. After completing all the configuration, enable the connection.
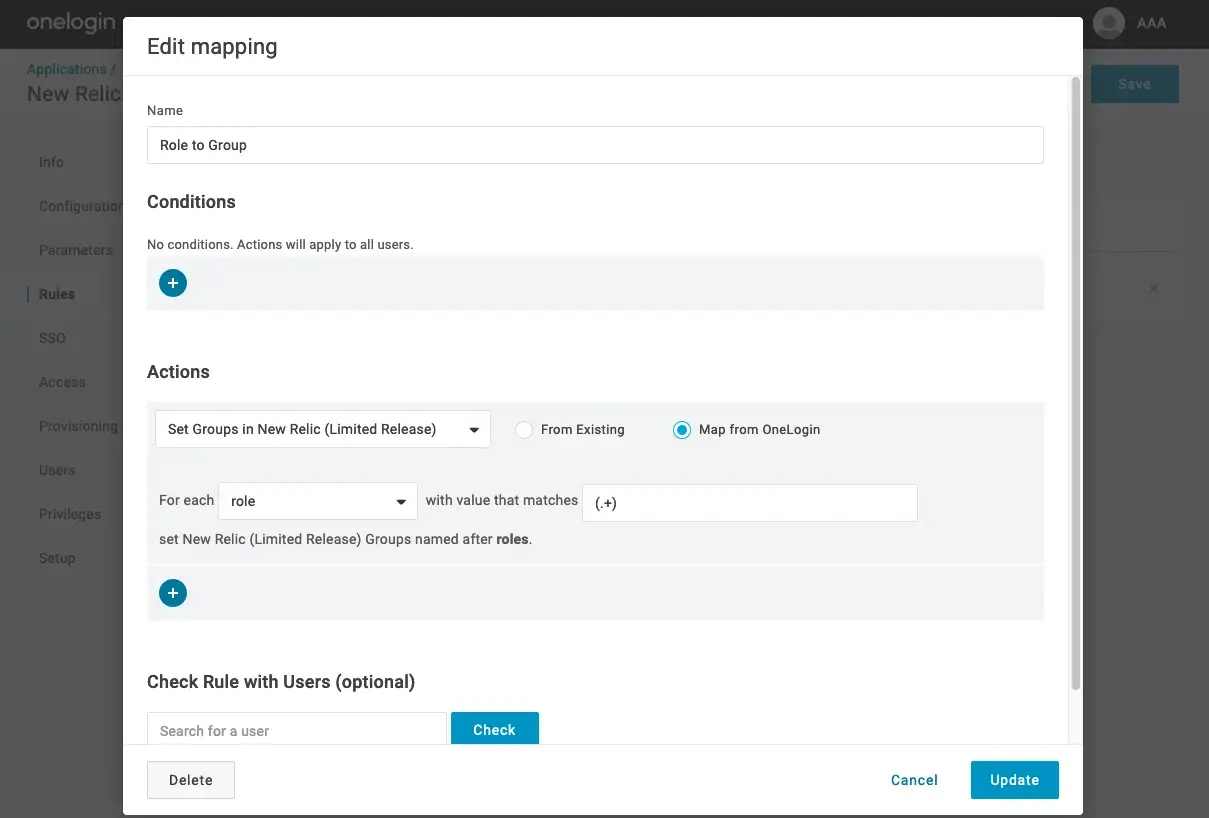
Fill in the rules form
Configure the user groups to send to New Relic using rules. OneLogin provides this documentation which describes how to use rules to provision groups for users.
Decide what type of groups to send along with your users to New Relic. If your organization is using Active Directory or LDAP, you might choose to use security groups to define your users permissions at New Relic. Another reasonable group choice is OneLogin role.
On the New Relic side, your user's groups define their permissions. The groups that are sent with users will be mapped to New Relic groups.
Note that at the moment, there is no way to delete a group from the OneLogin side. This is a known limitation from OneLogin. Removing or changing rules does not delete groups already sent to New Relic. If you wish to no longer use a group, removing all the users from the group will prevent it from being used at New Relic.
Fill in the provisioning form
In the left pane, select Provisioning and complete the following:
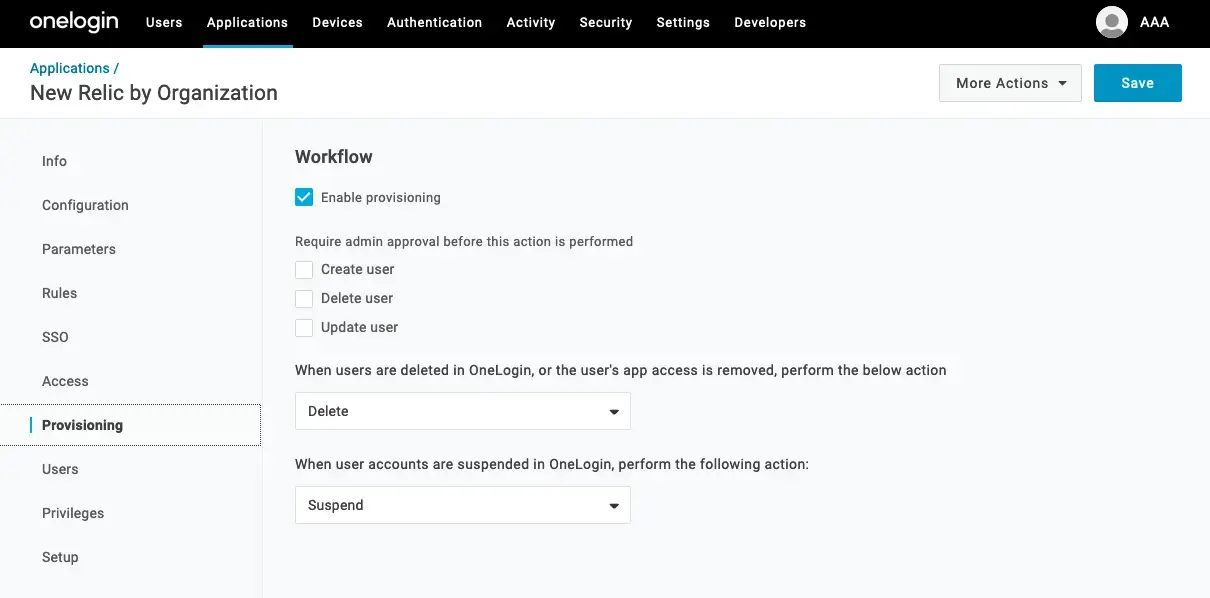
Check Enable provisioning.
Under Require admin approval before this action is performed, uncheck these options:
Create user
Delete user
Update user
Tip
If you do not uncheck these options, SCIM provisioning requests will not be sent until an administrator approves them.
Set When users are deleted in OneLogin, or the user's app access is removed, perform the below action to Delete.
Set When user accounts are suspended in OneLogin, perform the following action to Suspend.
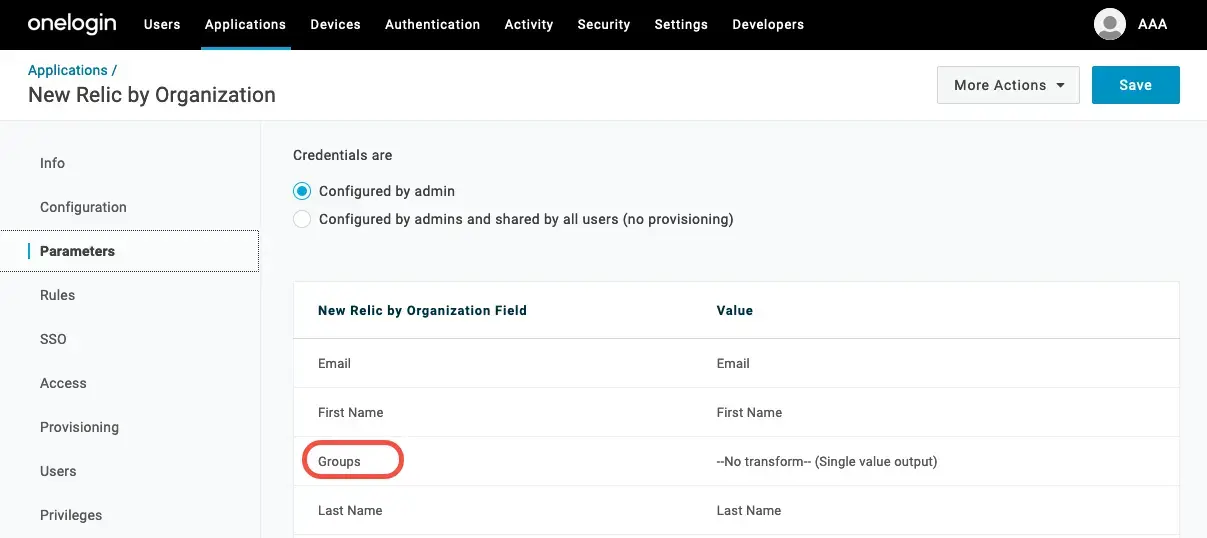
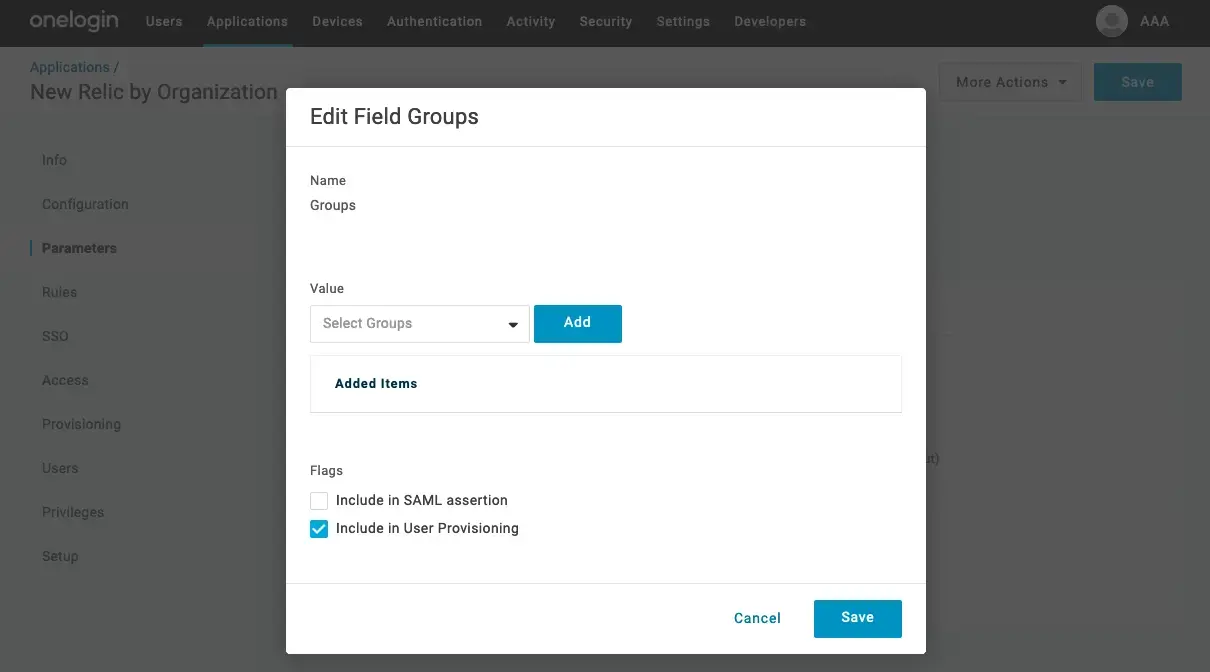
Fill in the Parameters form
In the left pane, select Parameters and complete the following:
Save your changes
After you complete the above forms, click Save. Then, return to the Configuration form and enable the API connection.
Step 4. Assign users
After New Relic SCIM/SSO application configuration is finished and New Relic side configuration is finished, you can begin to assign users to the application.
Assign the New Relic SCIM/SSO application to a user:
- Go to the OneLogin web site and sign in with an account that has administrator permissions.
- From the OneLogin home page, click Administration.
- From the OneLogin Administration page, choose the Users menu Users item.
- From the OneLogin Users page, click the user you want to assign the application to.
- From the user's page, click Applications.
- From the user's application page, click the plus sign and select the "New Relic by Organization" application.
- Important: Updating users' time zones is important because many New Relic features make use of that setting. The default format is UMT. From the Edit New Relic by Organization login for user page, enter the user's time zone in IANA Time Zone database format (also known as the Olson time zone database format) and click Save. Your users also have the ability to set their own time zone.
- If you're using Roles to define your New Relic groups, from the user's application page, click the proper role(s) for the user and then click Save User.
Step 5. Set your users' user type
When your users are provisioned in New Relic, you're able to see them in the User management UI.
If you're adding users to New Relic via SCIM but not managing their user type via SCIM, they start out as basic users. To upgrade users, you have two options:
- Use the User management UI to edit users.
- Configure the OneLogin app to manage user type.
Step 6. Assign group access
Once these steps are completed, you should be able to see your users in New Relic by going to the User management UI. Now that your users are present in New Relic, you must grant them access to specific roles on specific accounts. If this is not done, your users don't yet have access to New Relic. To learn how to do this, see:
Step 7. Configure SAML SSO
To enable SAML SSO for your users, see the SAML instructions.