New Relic は、あらゆるエンタープライズまたはテレメトリーデータのストリームに関する問題について情報を得ることができる柔軟なシステムです。 監視するデータ、超過した場合に問題となる閾値、通知先、通知方法を定義します。 アラートは、潜在的な問題を積極的に検出して対処するための動的なツールをチームに提供します。 アラートは、異常なアクティビティを特定し、関連する問題を関連付け、根本原因の分析を支援することで、システムをスムーズに稼働させるための迅速な対応を可能にします。
New Relicのアラートは、何が重要かを把握し、抑制されたノイズを管理し、アラート疲れを軽減するのに役立ちます。
アラートを使用すると、次のことが可能になります。
- 信号がしきい値と比較して評価されるように、または信号が異常な動作を示すかどうかを構成します。
- タグ付けしてアラートを整理します。
- より広範な問題に発展する前に、 異常を特定します。
- 通知を使用して、問題を正しいシステムまたはチームにルーティングします。
New Relic アラートを使用すると、次のことが可能になります。
- 追加の New Relic データを使用して問題の通知を強化します。
- データを正規化し、関連するインシデントをグループ化し、それらの間の関係を確立します。
- 受信したインシデントを関連付けます。
- 根本原因の分析を提供します。
- ノイズの多いアラートを削減および抑制します。
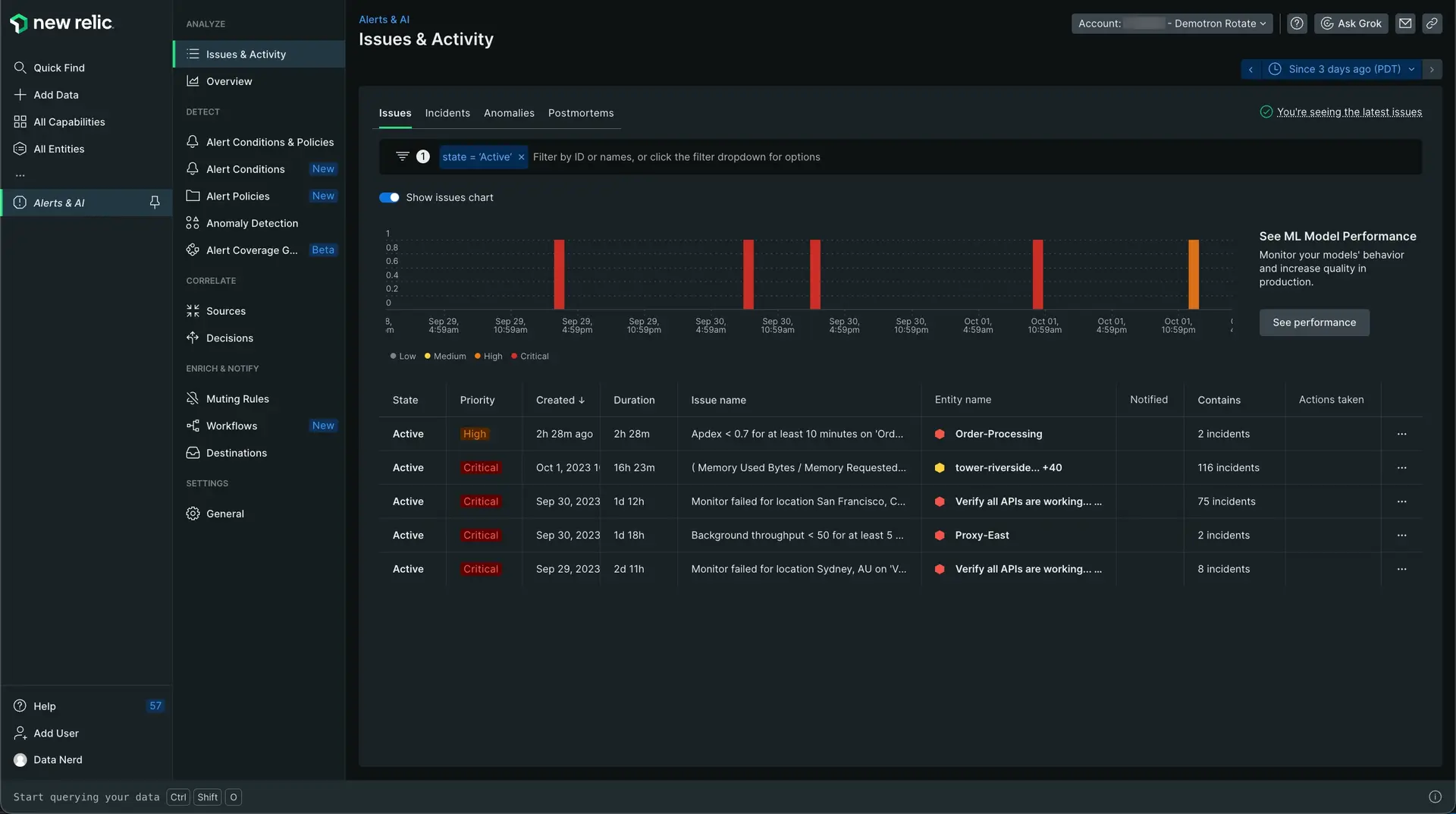
アラートを表示するには、 **one.newrelic.com > Alerts **に移動してください。
アラート条件を設定して通知を受信するには、いくつかの手順を実行する必要があります。開始するために必要なすべての手順については、チュートリアル シリーズをご覧ください。
最初のアラートの作成を始めてみませんか?最初のアラートを作成する方法をご覧ください。
アラートの概念と用語
インシデントは、アクティブなアラート条件のしきい値が満たされると生成されます。類似または関連するインシデントを問題に関連付け、アラート条件をグループ化してアラート ポリシーを作成できます。
ワークフローを通じて通知を構成して、アラート条件のトリガーについて通知できます。これらの通知には、適切なグループに連絡して問題の優先順位付けを支援するために、さまざまなチャネルに通知を送信するオプションが含まれています。
アラートを最大限に活用するには、いくつかの基本的な用語と概念を理解することが不可欠です。
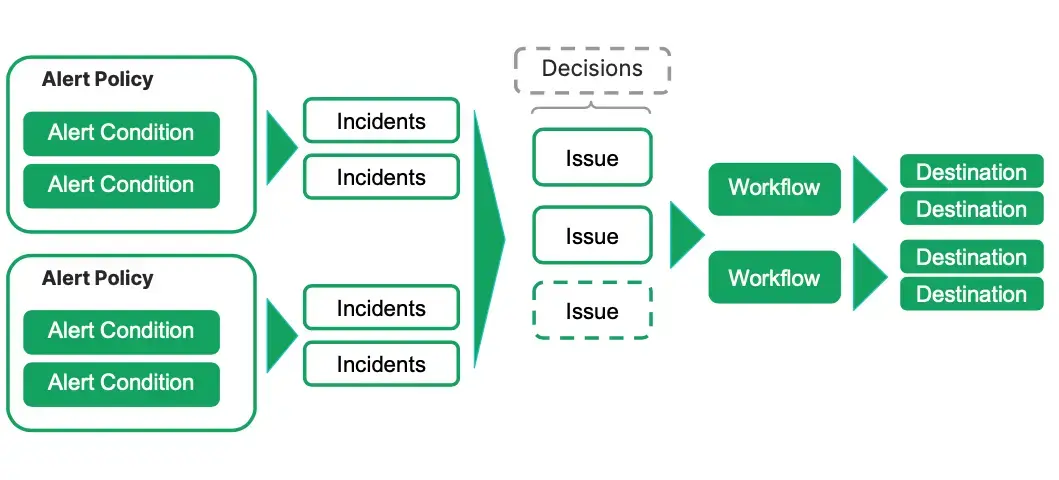
この図は、アラートがどのように機能するかを示しています。1 つまたは複数のアラート条件を含むアラート ポリシーを作成します。アラート条件には定義済みのしきい値が含まれており、そのしきい値に違反するとインシデントがトリガーされます。ワークフローを構成している場合は、通知を受け取ります。インシデントを問題にグループ化し、問題を意思決定にグループ化して、アラートをより適切に管理できます。
学期 | 説明 |
|---|---|
信号に適用される 1 つ以上のしきい値の構成。しきい値に違反すると、インシデントが作成されます。 | |
インシデントをより大きな問題にグループ化する論理的な操作。組み込みの決定があり、独自のカスタム決定を作成することもできます。 | |
お知らせを受け取るサービスです。これは、使用するサードパーティ システムの一意の識別子です。 | |
New Relic アラート条件または外部監視システムによって定義された状態変化またはトリガーを示します。イベントには、影響を受けるエンティティに関する情報が含まれます。 | |
条件のしきい値に違反したときに生成されるイベント。これは、問題の症状を詳細に示す個別のイベントです。 | |
注意と調査が必要で、通知が発生する 1 つ以上のインシデントの収集。 | |
インシデントが開始、承認、または終了したときに受信するメッセージ。 | |
インシデントの発生時に通知を受け取るように構成するアラート条件のグループ。 | |
インシデントをトリガーするためにデータ ソースが渡す必要がある値、およびインシデントを定義する時間関連の設定。 | |
問題に関する通知をいつ、どこで受信するかの定義。追加および関連する New Relic データを使用して通知を充実させることができます。 |
New Relic を実際に試してみませんか? 無料のNew Relicアカウントにサインアップし、クイック リリース ガイドに従って、今すぐデータを最大限に活用しましょう。 サポートが必要な場合は、アラートの作成に関するチュートリアル シリーズをご覧ください。
ヒント
Datadog を使用してログを監視していますが、New Relic の可観測性機能を無料で試してみたいと考えていますか?Datadog からの移行に関するガイドを参照してください。