Modern software is composed of thousands of components, and legacy security offerings don’t provide the necessary insight to monitor and remediate vulnerabilities these components introduce efficiently. With New Relic Security Remediation Explorer (Security RX), engineers from DevSecOps, SREs, and InfoSec teams can collaborate faster, identifying, triaging, and remediating vulnerabilities across your estate.
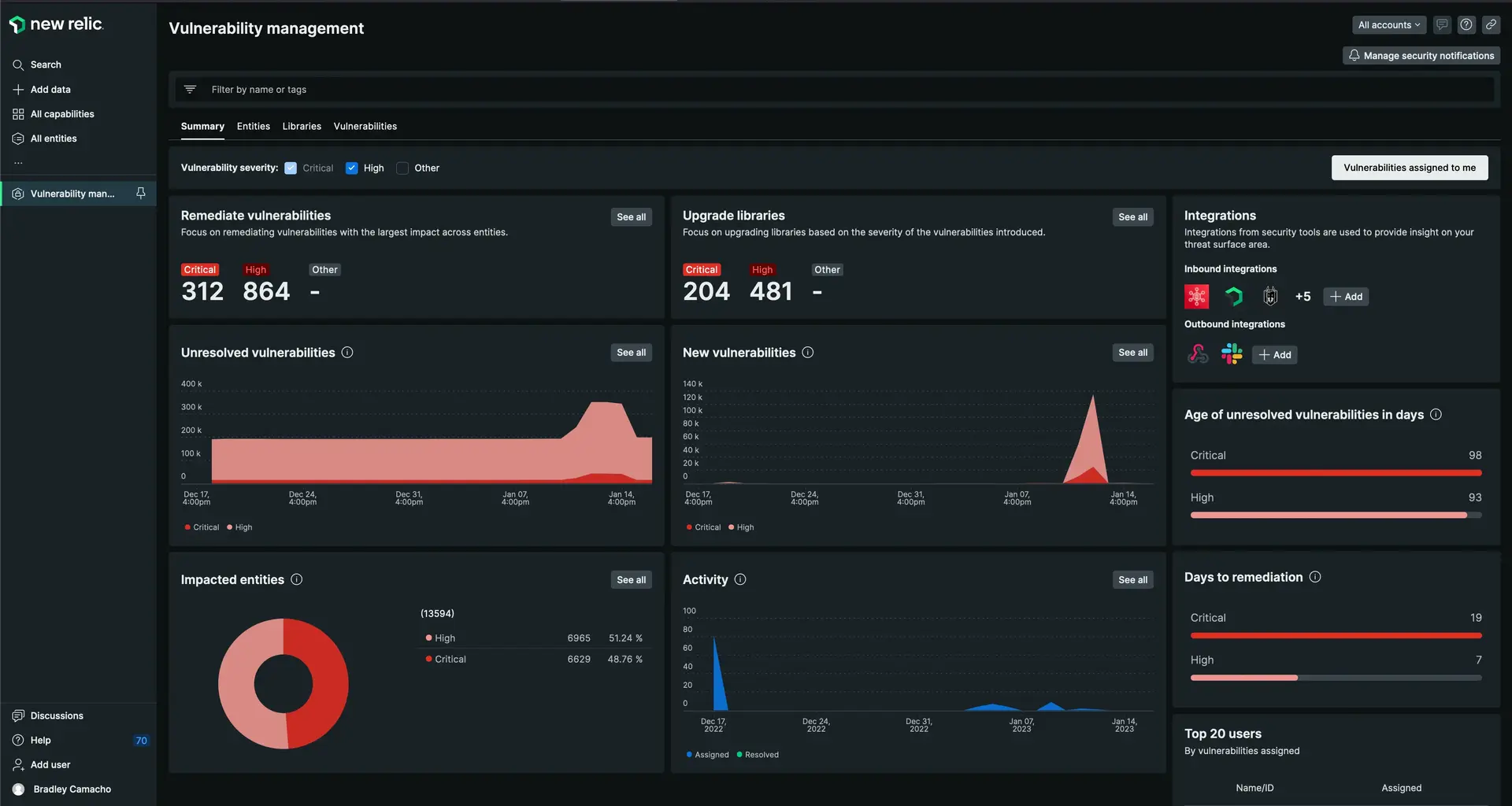
one.newrelic.com > All capabilities > Security RX
With Security RX, you get:
A birds-eye view of all vulnerabilities, including the ones that are detected by the New Relic platform and our integration partners such as FOSSA, AWS Security Hub, Trivy, Snyk, Dependabot, and more.
Continuous run-time visibility of vulnerabilities in your applications, infrastructure, and cloud environments
Near real-time deployment validation of security patches
With Security RX, overcome security blindspots across your entire stack from application to infrastructure without sacrificing velocity. Spend less time triaging false positives and low value findings, so your team can fix less and deliver more.
Visit one.newrelic.com to get started today.
View security insights for developers, security teams, and architects
As an engineer, you want to:
- Maintain a healthy application
- Identify the most urgent vulnerabilities in your software portfolio
- Understand the risk each vulnerability poses
- Surface "security" tasks from the security team in your daily workflow so it's easy to deliver more secure software with less toil
To dive deeper into these use cases, see:
As a member of a security team, you want to:
- Calculate the vulnerability surface area of your software systems
- Understand how runtime architecture of each application affects business risk, vulnerability, and severity
To dive deeper into these use cases, see:
What's next?
Ready to start using Security RX? Follow these steps:
Check prerequisites
Verify you have the required permissions and access
Set up integrations
Configure APM agents, Infrastructure agents, or third-party tools
Understand prioritization
Learn how vulnerabilities are ranked by CVSS, EPSS, and ransomware data
Security RX for Applications
Monitor vulnerabilities in your application dependencies
Security RX for Infrastructure
Monitor vulnerabilities in your OS packages and distributions
Security RX for Cloud
Monitor and remediate cloud misconfigurations in your AWS environment