The New Relic IAST exploitable vulnerabilities page informs you about the total number of critical and high vulnerabilites you have in your tested applications. To open the page, go to one.newrelic.com > All capabilities > IAST and click Exploitable Vulnerabilities on the left navigation pane.
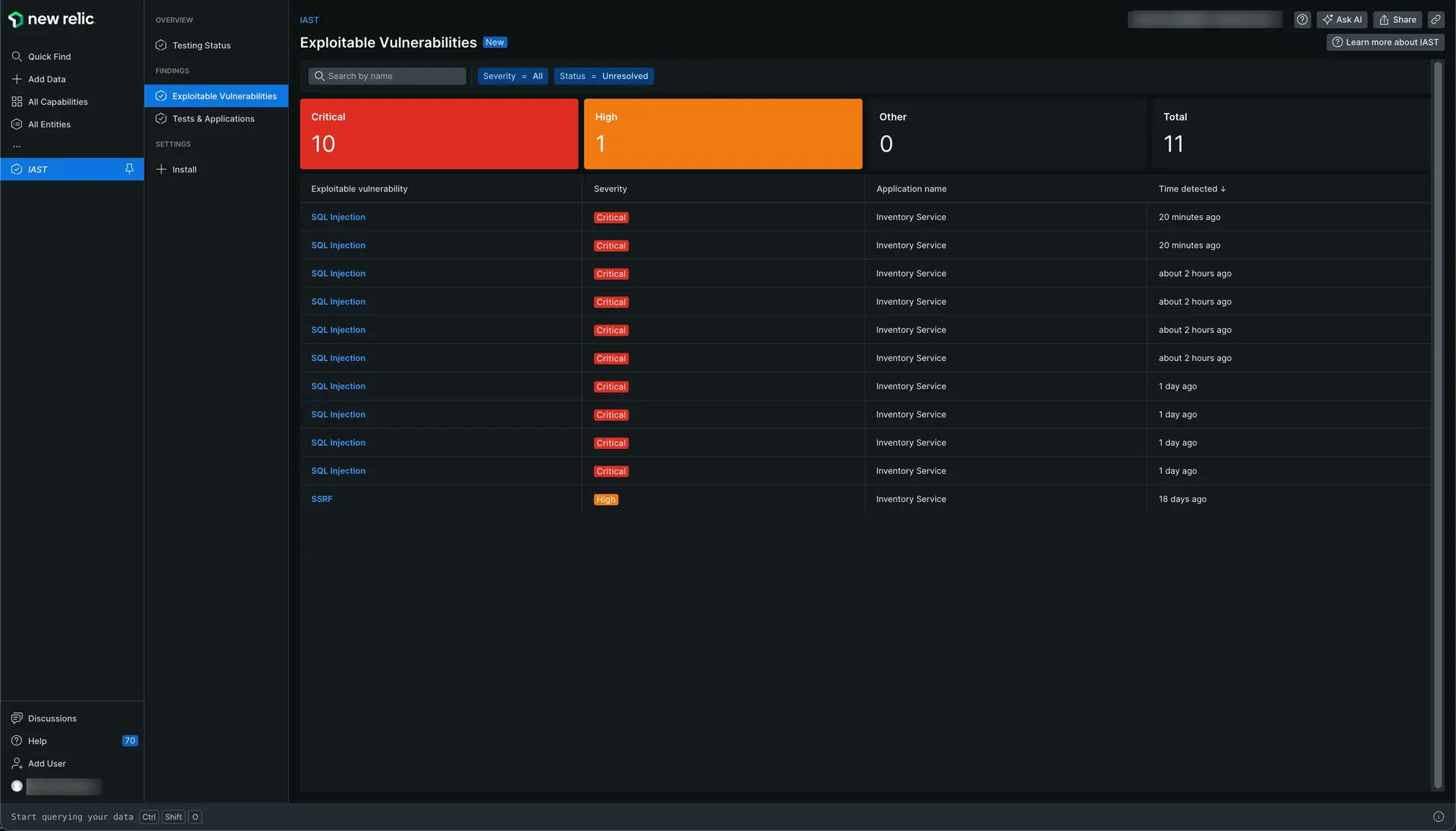
Go to one.newrelic.com > All capabilities > IAST and click Exploitable Vulnerabilities on the left navigation pane.
Details and remediation of a vulnerability
IAST provides out-of-the-box results with detailed vulnerability descriptions and detections down to the line of code. To see the details and the remediation instructions of a vulnerability:
Go to one.newrelic.com > All capabilities > IAST and click Exploitable Vulnerabilities on the left navigation pane.
Select an exploitable vulnerability to explore its details and understand how to address it. You can search the detected vulnerabilities by severity, exploitable vulnerability, application name or time detected. You can also order each column. The exploitable vulnerability details page gives you information about the details of that vulnerability, the stack trace, and the HTTP request of the vulnerability.
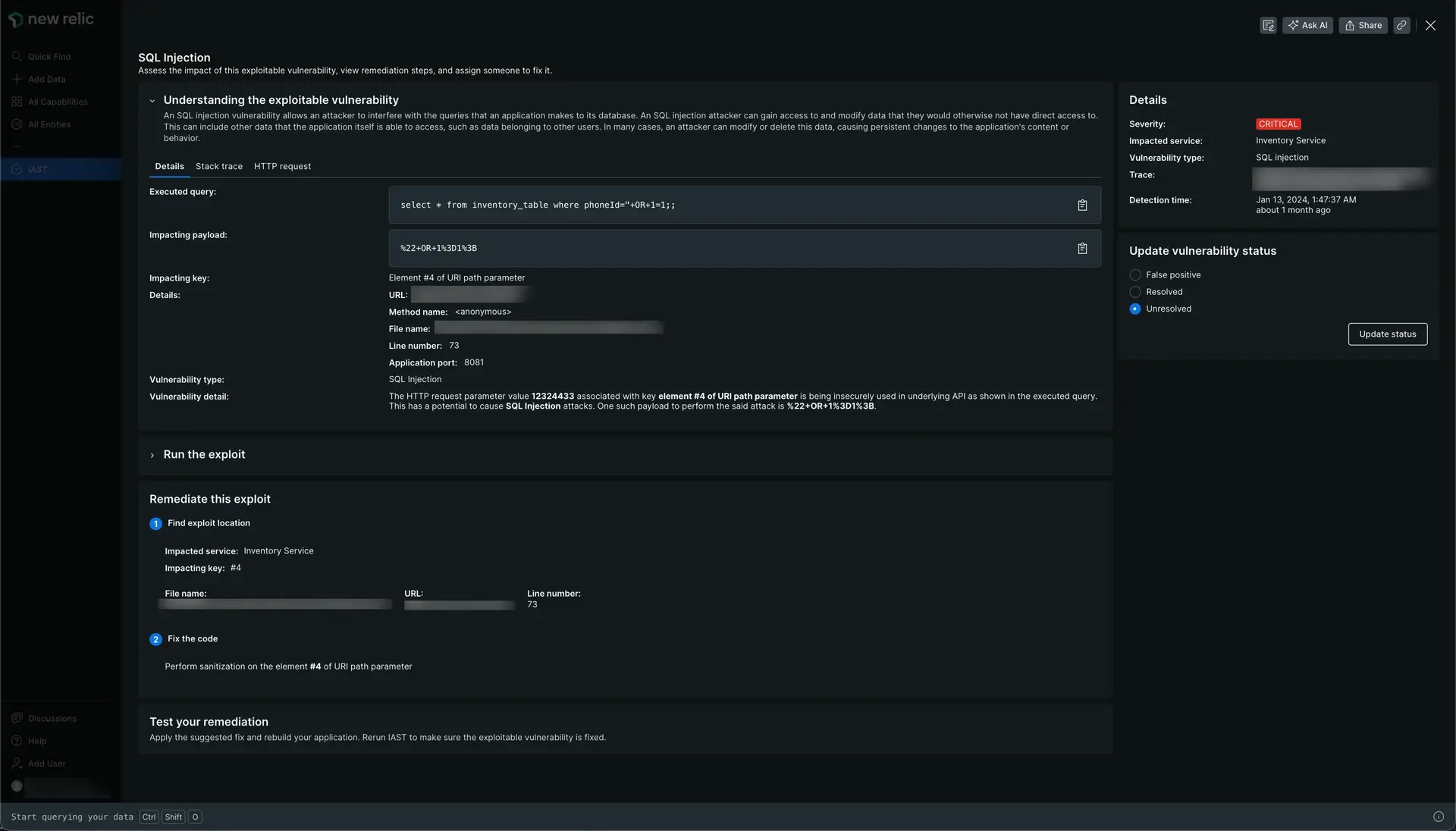
Expand the Run the exploit section to copy the curl you'll find here. You can use it to reproduce the issue as well as re-test once remediated.
Once you've applied the suggested fix, rebuild your application, and re-run IAST.
Ensure you update the status to mark the vulnerability status as either a false positive, resolved, or unresolved.