Alerts sends out timely notifications when your system is having problems. Sometimes you don't want to see some known notifications. You can use muting rules to stop being bombarded by messages that don't need your attention.
Once you've spotted the common elements in your unwanted notifications, you can define muting rules that specifically target those elements, while letting other notifications through. Even when a notification is muted, still gathers data on those alert events. Muting rules don't interfere with the alerts process and are applied at the point right before a notification is sent.
Create a muting rule
Important
Before creating muting rules, you'll need to create policies and conditions that generate notifications.
To create a muting rule, follow these steps:
Go to one.newrelic.com > All capabilities > Alerts and click Muting rules on the left navigation pane.
Click + Add a rule.
Enter a name and a description (optional) for the muting rule, and select the account to which the rule will apply.
Build the alert events filter. You can use a subset of alert event attributes. Choose an attribute, an operator, and a value. These are the attributes:
accountId,conditionId,conditionName,conditionType,entity.guid,nrqlEventType,nrqlQuery,policyId,policyName,product,runbookUrl(asconditionRunbookUrl),tags.<NAME>, andtargetName). Values are compared against one of your alert event attributes, such as an alerts policy ID or a condition name.Click Add another condition if you want to include more filters.
Manage muting rules
A muting rule condition is the set of individual expressions made up of attributes, operators, and values that define which alert events to target for muting.
To create, enable, disable, and manage muting rules, follow these steps:
Go to one.newrelic.com > All capabilities > Alerts and click Muting rules on the left navigation pane.
Enable or disable muting rules at any time from the Enabled column. You also can edit each rule by clicking the icon on the row of each rule.
Rules can have one of the following statuses:
- Active: Muting is enabled and active.
- Scheduled: Muting is enabled but not active yet (there's a future schedule).
- Ended: Muting is enabled, but no longer active (there's no future schedule).
- Inactive: Muting is disabled.
Notification options for muting rules
When a muting rule is active, and an alert event is opened, a user will not receive a notification. You can configure the behavior for notifications when a muting rule is inactive with the two settings below:
Notify: If there’s an ongoing alert event after the muting rule window ends, you will be notified. This works by closing the existing, muted alert event, and if the threshold is still being violated, a new alert event will open in a non-muted state, triggering a notification. We recommend keeping this default setting.
Suppress notification: If there’s an ongoing alert event after the muting rule window ends, you will not be notified. This works by leaving the existing, muted alert event open past the muting rule window end timestamp.
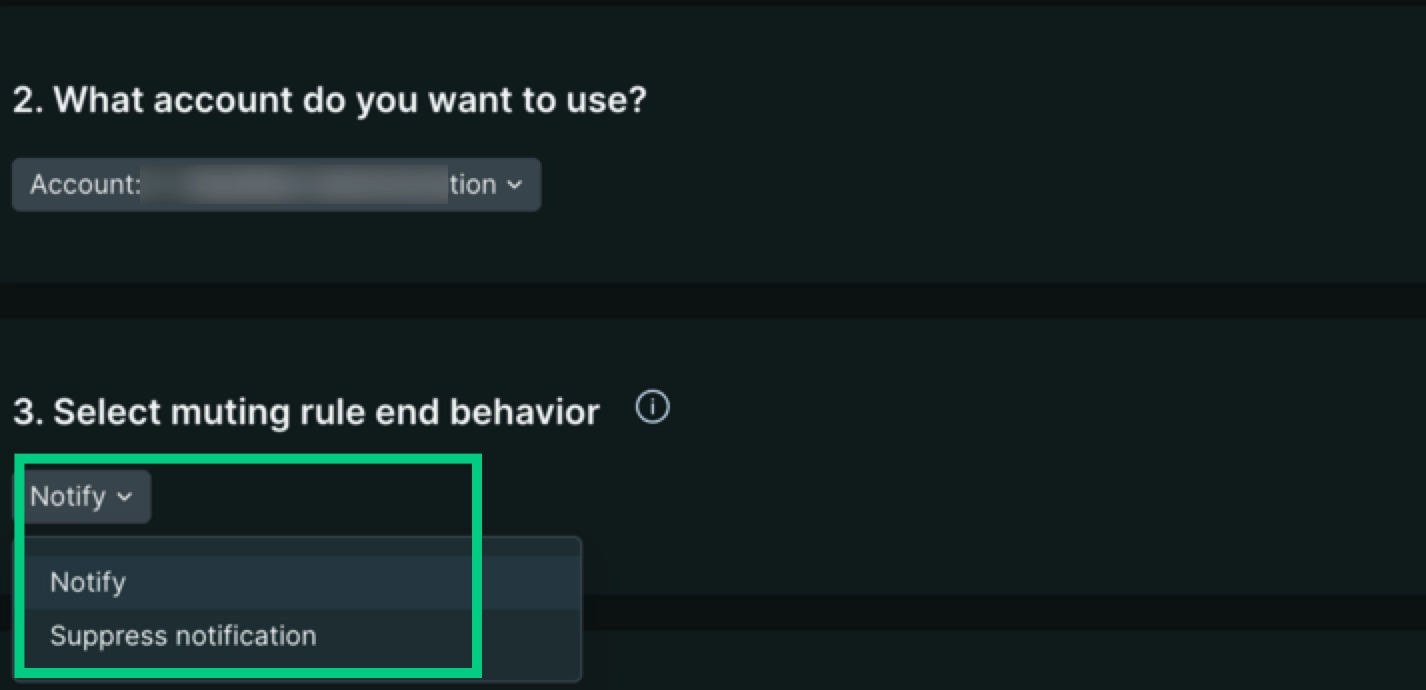
Go to one.newrelic.com > All capabilities > Alerts and click + Add a rule.
Schedule a muting rule
If needed, you can schedule your muting rules.
To do this, select a start time and end time. Optionally, you can set the muting rule to last an entire day.
You can also choose to select a time zone for the muting rule schedule. The default is the time zone selected in your user preferences.
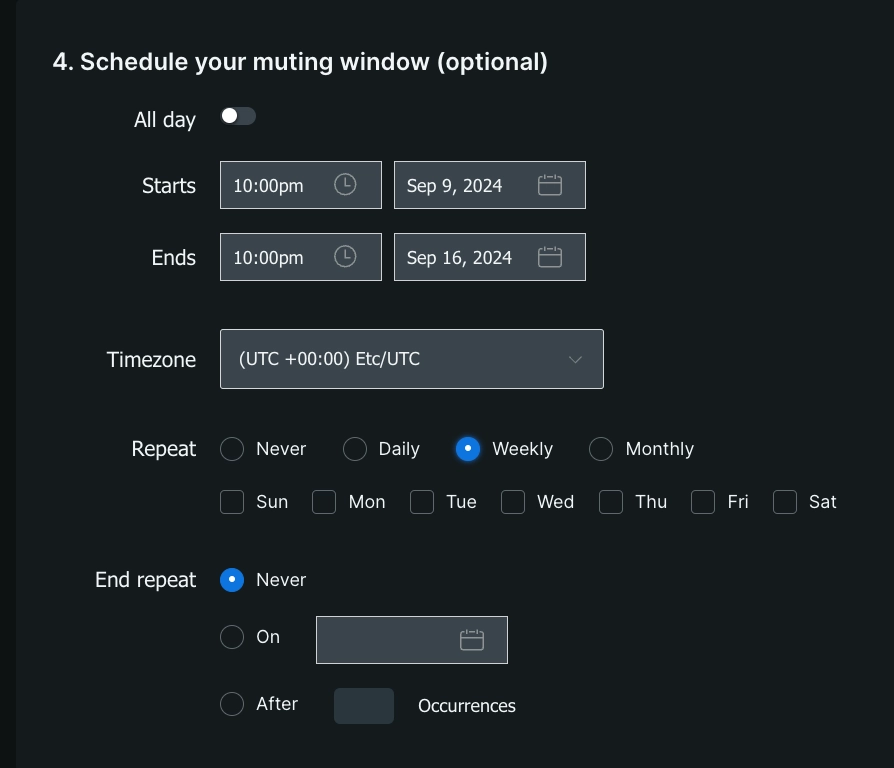
Go to one.newrelic.com > All capabilities > Alerts and click Muting rules on the left navigation pane. Check the flexible and powerful options you have for scheduling your muting rules.
You can schedule your muting rules to recur daily, weekly, or monthly. A muting rule that's scheduled to repeat weekly includes the option to select the days of the week to recur. If no days are selected, the weekly recurrence will default to repeating on the day of the week that the muting rule is scheduled to start.
Important
The Repeat day of the week checkboxes override the Starts and Ends date fields. If you set a start date and also choose a day of the week, your muting rules will be applied on the first of those days after your start date.
You can also specify when you would like recurrence to end by selecting either a specific date or a certain number of occurrences.
View muted alert events and issues
When viewing an open or closed issue, alert events and issues are marked as Muted. You can view muted alert events and issues in the following locations:
View a muted issue: Go to one.newrelic.com > All capabilities > Alerts and click Issues & Activity on the left navigation pane. Click on any muted issue to see details about the critical alert events that have been muted.
View a list of muted alert events: Go to one.newrelic.com > All capabilities > Alerts and click Issues & Activity on the left navigation pane. Then select the alert events tab. Muted alert events and issues are marked with the icon in the Muted column.
Mute faceted results using tags.
To mute results of faceted queries, use the tags.FACETED_ATTRIBUTE attribute, where FACETED_ATTRIBUTE represents the attributed you've run a NRQL FACET query on. For example: if your NRQL alert condition includes FACET host in its query, you can target that FACET attribute using tags.host.
NRQL condition queries can accept multiple facet attributes. If you want to be able to filter from attributes in your events or metric time series that have been aggregated, you must add those attributes to your NRQL query FACET clause; for example: FACET host, region, cluster.
For an example of using tags., see Create muting rule.
Sub-condition operators
These are the logical operators you can use to compare attributes when you're adding muting rules. If you're new to muting rules, see these examples.
Tip
All sub-condition operator values are case-sensitive. For example, if you use policyName STARTS_WITH 'PROD' a policy name that starts with 'Prod' won't get picked up.
EQUALS: Where the supplied value equals the alert event attribute value.DOES_NOT_EQUALS: Where the supplied value doesn't equal the alert event attribute value.IN: Where the alert event attribute value is present in a list of supplied values (up to 500).NOT_IN: Where the alert event attribute value isn't present in a list of supplied values (up to 500).CONTAINS: Where the supplied value string is present in the alert event attribute value.DOES_NOT_CONTAINS: Where the supplied value string isn't present in the alert event attribute value.ENDS_WITH: Where the alert event attribute value ends with the supplied value string.NOT_ENDS_WITH: Where the alert event attribute value doesn't end with the supplied value string.STARTS_WITH: Where the alert event attribute value begins with the supplied value string.DOES_NOT_STARTS_WITH: Where the alert event attribute value doesn't begin with the supplied value string.IS_BLANK: Where the alert event attribute value is blank. Null, empty string, etc.IS_NOT_BLANK: Where the alert event attribute value is not blank. Null, empty string, etc.IS_ANY: A condition with this operator will mute all alert events on the account.
How muting rules work
Muting rules are applied at the end of the default alert lifecycle in order to suppress or mute notifications. They don't disable existing policies or conditions. For example, you can mute notifications during known system disruptions, such as maintenance windows and deployments. System disruption alert events will still be identified, even though the notifications for those alert events are muted.
A muting rule uses a set of conditions that match against attributes in an alert event. The muting rules tell us how to:
- Identify individual alert events after they're created, but before an issue is opened.
- Override their default condition to indicate that they should be muted.
Currently, muting an alert event means that the normal alerting event lifecycle is maintained, except that an issue containing only muted alert events will not send any notifications.
Muting rules are determined by the first event that triggered a notification within an issue. This means that if the first notification event was muted due to a muted state, the rest of the issue will be muted as well.
Muting rules override specific alert events. They don't disable existing policies or conditions. This allows you to mute alert events from specific entities that may be covered by a policy or condition that covers a large number of entities. This also keeps you from having to over-mute your monitoring when you are performing maintenance on a subset of your system.
The following table describes how the alerts event lifecycle is affected by muted alert events:
IF | THEN | |
|---|---|---|
Event: Issue is activated | ||
An issue is activated because of an alert event that is not muted | Notifications for this issue will be sent. | |
An issue is activated due to an alert event that is muted | Notifications for this issue will not be sent (muted). | |
Muting behavior with workflows
A triggered alert event has a 1:1 ratio with an issue so if an alert event is muted then the matching issue will be muted as well. Workflows are triggered by issues that can have one or more alert events, therefore there could be a scenario of muted and not muted alert events combined.
Each issue has one of the following muting states:
- Fully muted (
FULLY_MUTED): an issue has all of its open alert events muted (Default value). - Partially muted (
PARTIALLY_MUTED): an issue that has at least one open alert event that is muted and one open alert event that is not muted. - Not muted (
NOT_MUTED): an issue that has no open muted alert events.
For a step-by-step guide on how to set up your workflows, check out an example demo below (approx. 2:17 minutes):
Muting behavior with NerdGraph
In NerdGraph, you can use the following queries and mutations with your muting rules. You can see the schema in more detail in the API Explorer.
actor.account.alerts.mutingRule: Fetch a muting rule by ID.actor.account.alerts.mutingRules: Fetch a list of muting rules for an account.alertsMutingRuleCreate: Create a muting rule for an account.alertsMutingRuleUpdate: Update a muting rule by ID and account ID.
You can find some sample queries and mutations examples in this page.
A muting rule has the following fields and components:
Muting rule | Fields and components |
|---|---|
| The muting rule's account ID. A muting rule will only affect alert events that occur in a single account. To mute alert events across multiple accounts, you'll need to create a muting rule for each account separately. |
| The expected behavior at the end of the muting rule window. Valid values of |
| The set of individual expressions that define which alert events to target. A muting rule condition includes:
|
| The timestamp when the muting rule was created (UTC). |
| The user ID of the person who created the muting rule. |
| This is an optional text field describing the muting rule. It's a useful way to provide more context for your muting rule. This data is only used for management display purposes. |
| Enable or disable the muting rule (Boolean). Enable and disable your muting rules manually. |
| The unique identifier for the muting rule. |
| A datetime stamp representing the last time the muting rule window end behavior was applied. |
| A text field for the user-friendly name of the muting rule. This is used when listing or referencing a rule. We don't require that the name be unique, but it's recommended. |
| The time window when the
|
| The timestamp when the muting rule was last modified (UTC). |
| The user ID of the person who last modified the muting rule. |
Muting examples
For more information about making requests to NerdGraph, see the NerdGraph documentation, including GraphQL tutorials.