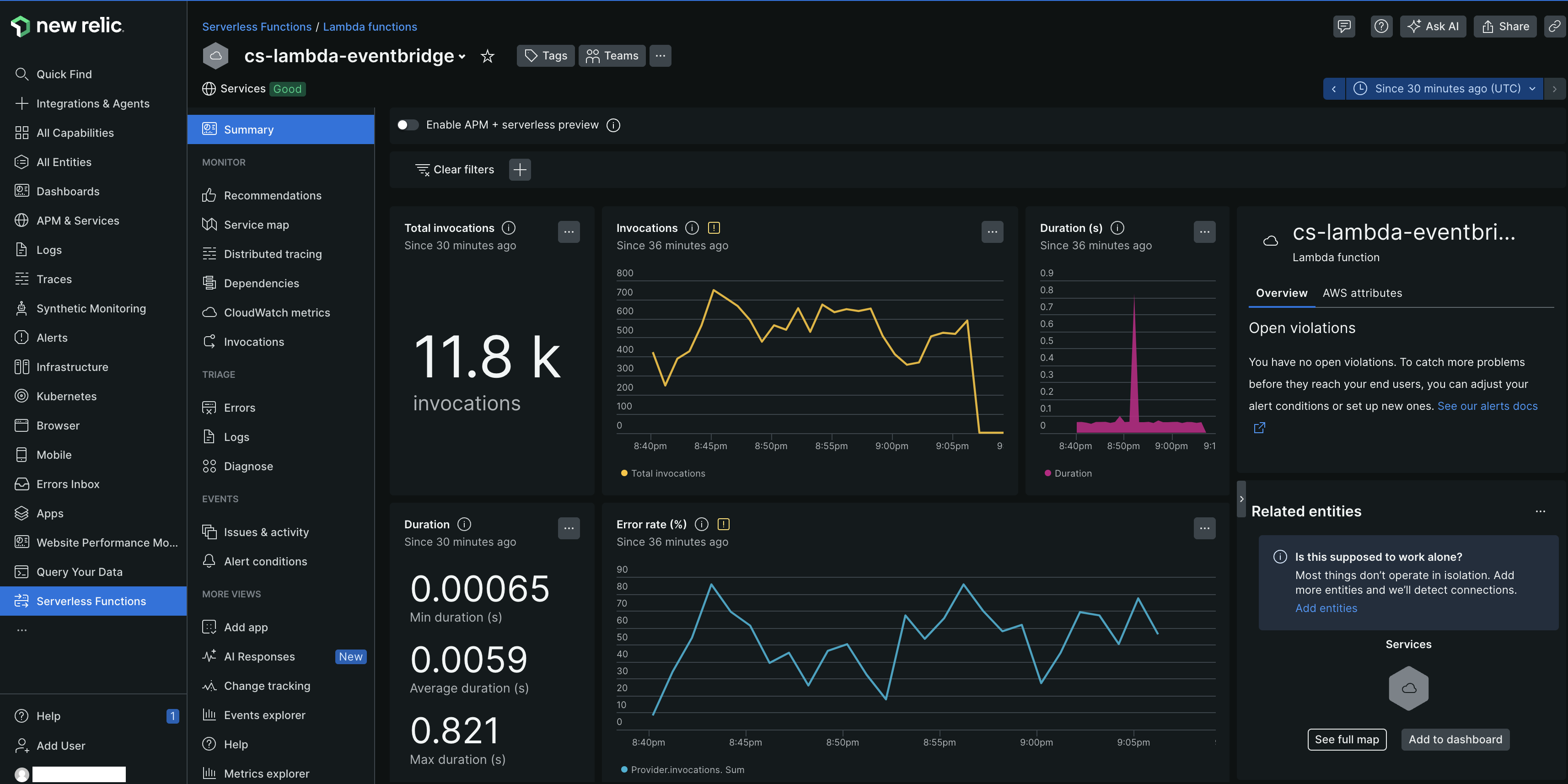
New Relic's instrumentation for AWS Lambda offers deep visibility into the inner workings of your functions. By adding the New Relic agent to your function, each invocation is monitored by New Relic. This enables you to track the duration of function invocations, monitor errors, and record details about the source events and your function's responses.
Shipping methods for Lambda telemetry
There are three primary methods to ship telemetry data from AWS Lambda to New Relic, each with its own cost and reliability considerations:
- Cost-Effective Method: Utilize New Relic's layers, including the Lambda extension, which avoids sending data to AWS CloudWatch by default.
- Reliability-Focused Method: Disable the New Relic Lambda extension and use CloudWatch exclusively to ship data, reducing the Lambda function's overhead.
- Hybrid Method: Combine the extension with CloudWatch as a fallback, balancing cost efficiency with reliability.
Cost consideration
Implementing serverless monitoring for AWS Lambda may incur additional AWS charges. The newrelic-log-ingestion Lambda function, which reports data to New Relic, is considered a third-party service, and any associated AWS charges are the user's responsibility.
By using the newrelic-lambda-extension included in New Relic Lambda layers, you can avoid sending logs and telemetry data via CloudWatch, although configuring the newrelic-log-ingestion function as a CloudWatch fallback is possible for high availability needs.
Enabling serverless monitoring for AWS Lambda may result in Amazon Web Services charges. Our newrelic-log-ingestion Lambda function, which reports your Lambda data to us, is considered a Third Party Service: AWS charges resulting from your use of it are your responsibility.
If you use our newrelic-lambda-extension bundled in our New Relic Lambda Layers, you can avoid sending logs and telemetry via CloudWatch and the newrelic-log-ingestion function. It's also possible to configure the newrelic-log-ingestion function as a CloudWatch fallback method for functions that require high availability of observability data.