New Relic アカウントとAWSアカウントを正常にリンクしたら、New Relic Lambdaレイヤーを追加してLambda関数を実装できます。 これにより、New Relic エージェントが統合され、関数が呼び出されるたびに自動監視が可能になります。
あなたが始める前に
インストゥルメンテーション方法
New Relic包括的な監視のためにAWS Lambda 関数をプランニングするためのいくつかの方法を提供しています。
- コマンドラインインターフェース (CLI) : AWS CLI を使用して、 New Relicレイヤーを Lambda 関数にすばやく追加します。
- サーバーレス フレームワーク: New Relicインストゥルメンテーションをサーバーレス エンタープライズにシームレスに統合します。
- CloudFormation/SAM : インフラストラクチャ コード テンプレートにNew Relicレイヤーを含めます。
- AWS CDK : 他のインフラストラクチャリソースとともに、CDK コードに New Relic Lambda レイヤーを追加します。
- Terraform : New Relicインストゥルメンテーションを他のインフラストラクチャ リソースと一緒に簡単に管理します。
- 手動インストゥルメント : よりきめ細かな制御を行うには、 コンソールからNew Relic AWS Lambdaレイヤーを直接追加します。
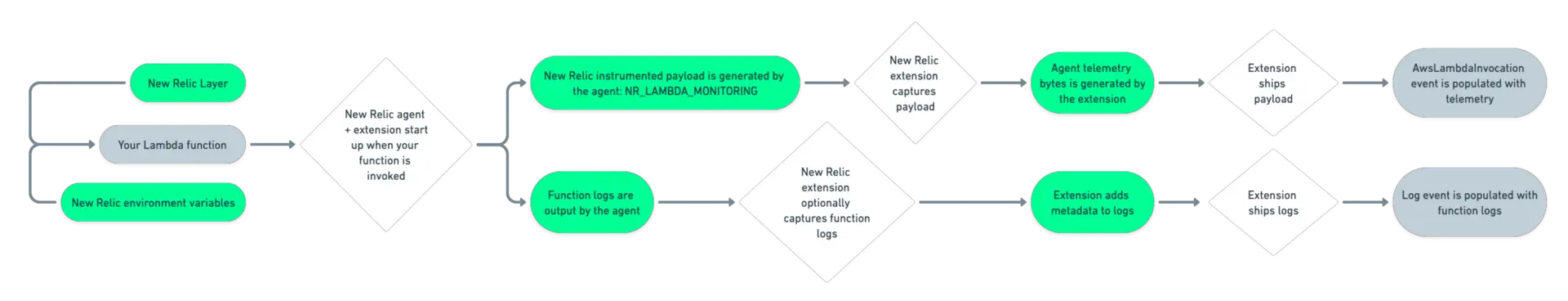
選択した方法に関係なく、New Relic レイヤーは関数に New Relic エージェントを追加します。 このエージェントは、呼び出し時に関数を自動的にインストゥルメントし、ペイロード NR_LAMBDA_MONITORING を生成して、 New Relic Lambda 拡張機能を介してNew Relicに送信します。
ニーズに応じて、拡張機能をバイパスして CloudWatch でテレメトリーのみを表示するか、CloudWatch をバイパスするか、CloudWatch をフォールバックとして使用するかを選択できます。 このドキュメントの最後にあるCloudWatchセクションで、各オプションについて説明します。
newrelic-lambda CLI クイックスタートを使用して Lambda 関数を計算できます。
New Relicインストゥルメンテーション レイヤーをインストールまたはアップグレードするには、次のコマンドを実行します。
$newrelic-lambda layers install --nr-account-id YOUR_NR_ACCOUNT_ID --function my-function --upgradeこのコマンドは、Lambdaのリージョンとランタイムに合わせて、利用可能な最新のレイヤーを自動的に見つけます。
このコマンドは、 New Relicインストゥルメントを迅速に開始する方法を提供し、 CI/CDパイプラインに簡単に統合できます。 ただし、既存の Lambda 関数リソースが変更されるため、更新されたコードを再デプロイすると、インストゥルメンテーションが誤って削除される可能性があります。 継続的な監視を確実に行うには、各インストーラの後にコマンドを再実行するか、可能であれば、 New Relicレイヤーと設定をインストーラ プロセスに直接組み込みます。
CLIはバッチで多くの関数を操作できることに注意してください。 --function all 、 --function installed 、または--function not-installedを使用して、リージョン内のすべての関数を操作するか、既存のNewRelicインストルメンテーションの有無にかかわらず関数のみを操作します。
AWSのサーバーレスアプリケーションモデル(SAM)は、CloudFormationテンプレートの一種であり、機能を依存するリソースに関連づけたり、アプリケーション全体のライフサイクルを管理したりすることを容易にします。私たちはLambdaのサンプル関数のほとんどにSAMとCloudFormationを使用しており、他の多くのツールはCloudFormationテンプレートの上に構築され、抽象化の追加レイヤーを提供しています。
CloudFormation は、 AWSリソースのプロビジョニングと管理を簡素化するAWSサービスです。 YAML または JSON テンプレートでリソースの望ましい状態を定義することにより、CloudFormation は基盤となるAPIコールを自動的に処理し、必要に応じてリソースを作成、更新、または削除します。 この宣言型アプローチにより、インフラストラクチャ管理が自動化され、一貫性と再現性が確保されます。
Node.jsLambda関数の単純なCloudFormationテンプレートの例を次に示します。
AWSTemplateFormatVersion: '2010-09-09'Transform: AWS::Serverless-2016-10-31Description: And example of a simple instrumented Node.js Lambda
Resources: NewRelicExample: Type: AWS::Serverless::Function Properties: # In this example, we're using the SAM CLI to package and deploy our lambda. SAM will transform this value during the publish step. CodeUri: newrelic-example-node/ # The handler for your function needs to be the one provided by the instrumentation layer, below. Handler: newrelic-lambda-wrapper.handler Runtime: nodejs12.x Environment: Variables: # For the instrumentation handler to invoke your real handler, we need this value NEW_RELIC_LAMBDA_HANDLER: YOUR_PATH_TO_INITIAL_LAMBDA_HANDLER # Distributed tracing needs your account ID, and your trusted account ID NEW_RELIC_ACCOUNT_ID: YOUR_ACCOUNT_ID_HERE # If your New Relic account has a parent account, this value should be that account ID. Otherwise, just # your account id. NEW_RELIC_TRUSTED_ACCOUNT_KEY: YOUR_PARENT_ACCOUNT_ID_HERE Layers: # This layer includes the New Relic Lambda extension, a sidecar process that sends telemetry, # as well as the New Relic agent for Node.js, and a handler wrapper that makes integration easy. - !Sub arn:${AWS::Partition}:lambda:${AWS::Region}:451483290750:layer:NewRelicNodeJS12X:34 Policies: # This policy allows the lambda to know the value of the New Relic license key. We need this so # that we can send telemetry back to New Relic - AWSSecretsManagerGetSecretValuePolicy: SecretArn: !ImportValue NewRelicLicenseKeySecret-NewRelic-LicenseKeySecretARN通常、関数とそのリソースを記述するtemplate.yamlという名前のファイルがあります。
Serverless フレームワークは、サーバーレス アプリケーション向けの人気のある開発およびデプロイメント ツールです。 これは AWS 向けに Node.js で記述されており、主に CloudFormation テンプレート上の高レベルの抽象化として機能します。 Node、Python、Ruby、Java、.NET 関数に適しています。
New Relic では、Serverless Framework アプリケーションのインスツルメンテーションを簡素化するために、 Serverless Framework Plugin を提供しています。
プラグインをインストールするには、次のコマンドを実行します。
$npm install --save-dev serverless-newrelic-lambda-layersまたは、代わりに次のコマンドを実行することもできます。
$yarn add --dev serverless-newrelic-lambda-layers次に、 New RelicアカウントIDとNew Relic個人APIキーを見つけます。
次に、 serverless.yamlファイルに次のコードを追加します。
plugins: - serverless-newrelic-lambda-layerscustom: newRelic: accountId: your-new-relic-account-id-here apiKey: your-new-relic-personal-api-key-here linkedAccount: your-new-relic-integration-account-name-hereAWSクラウド開発キット ( AWS CDK) は、クラウド リソースをコードで定義し、 AWS CloudFormation を通じてプロビジョニングするためのフレームワークです。
以下は、 New Relicインストゥルメントで行われた Node.js Lambda関数をデプロイする基本的な CDK アプリの例です。
import * as cdk from 'aws-cdk-lib';import { Construct } from 'constructs';import * as lambda from 'aws-cdk-lib/aws-lambda';
export class NewRelicExampleCdkStack extends cdk.Stack { constructor(scope: Construct, id: string, props?: cdk.StackProps) { super(scope, id, props); // Add latest New Relic Lambda layer ARN from https://layers.newrelic-external.com const NewReliclayerArn = 'arn:aws:lambda:us-east-1:451483290750:layer:NewRelicNodeJS20X:39'; const myFunction = new lambda.Function(this, "NewRelicExampleLambda", { runtime: lambda.Runtime.NODEJS_20_X, // Update functions handler to point to the New Relic Lambda wrapper handler: "newrelic-lambda-wrapper.handler", code: lambda.Code.fromAsset('lib/lambda-runtime-code'), layers: [lambda.LayerVersion.fromLayerVersionArn(this, 'NewRelicLayer', NewReliclayerArn)], environment: { // Set the NEW_RELIC_LAMBDA_HANDLER environment variable to the path of your initial handler. NEW_RELIC_LAMBDA_HANDLER: 'index.handler', }, }); }}Terraform は、コード ツールとしての一般的なインフラストラクチャとして人気の高いツールです。 AWS リソースの管理に使用できます。 Terraform スクリプトを使用して インストゥルメントされた Lambda 関数のデプロイの 例をいくつか 紹介します。New Relic
New Relic Terraform プロバイダーを使用して、 AWSインテグレーションをセットアップできます。
上記の方法よりもエラーが発生しやすく、手間がかかりますが、AWS LambdaコンソールからNew Relicを使用するようにLambda関数の設定を手動で変更することができます。Node.jsの場合、 Python、Ruby、Java。
New Relicランタイムに LambdaRuby を実装する方法の例を次に示します。
AWS ウェブコンソールのLambdaサービスセクションに移動します。 そこから、 New Relicに接続する Lambda関数 を見つけます。
デフォルトのCode [コード]タブで、 Layers [レイヤー]セクションまで下にスクロールし、 Add a layer [レイヤーの追加]ボタンをクリックします。
Create layer [レイヤーの作成]ボタンをクリックします。
Choose a layer [レイヤーの選択]に移動し、 Specify an ARN [ARN の指定]オプションを選択します。
New Relicのレイヤーリストに移動し、ドロップダウンリストを使用して、Lambda 関数がホストされているAWSリージョンを選択します。 そこから、Lambda 関数のRubyバージョンとアーキテクチャに一致する ARN を見つけます。 オプションは X86 と ARM64 の 2 つあります。 Copy to clipboard [クリップボードにコピー]ボタンを使用するか、ARN 文字列を手動でコピーします。
AWS コンソールフォームのSpecify an ARN [ARN の指定]セクションで、New Relic Lambda レイヤーの ARN を貼り付けます。
AWSコンソールフォームで、 Add [追加]ボタンをクリックして、Lambda 関数にレイヤーを追加します。
Lambda関数のページで、デフォルトのCode [コード]タブを選択した状態で、Runtime settings [ランタイム設定]セクションまで下にスクロールし、Edit [編集]ボタンをクリックします。
既存のHandler [ハンドラー]値の安全なコピーを作成します。 後の手順で必要になります。
Handler[ハンドラー]の値を
newrelic_lambda_wrapper.handlerに変更し、 Save [保存]をクリックします。Lambda関数のページのConfiguration [設定]タブに切り替えます。
Environment variables [環境変数] サブタブを選択し、要件に基づいてEnvironment variables [環境変数]を定義します。
実行ロールを変更して、 New Relicシークレットにアクセスできるようにします。
NEW_RELIC_LICENSE_KEYという名前のシークレットの ARN を見つけます。関数の実行ロールに、以下のコードのような新しいインライン ポリシーを追加します。
SECRET_ARNを上記で見つけた値に置き換えます。"Statement": [{"Action": ["secretsmanager:GetSecretValue"],"Resource": "SECRET_ARN","Effect": "Allow"}]ヒント
New Relicレイヤーは、 New Relic Rubyエージェントを自動的に配信し、Lambda 関数の呼び出し前にRuby
requireを介してロードされます。 競合を避けるため、Ruby エージェントのコピーを他の場所に含めないでください。 エージェントの存在を活用するために、関数内で必要なNew Relic RubyエージェントAPI呼び出しを自由に実行してください。
Java、Python、Node.js、および .Net ランタイムは、 Rubyと同じインストゥルメンテーション フローに従いますが、ハンドラーがいくつか異なります。 関数のコンソールで新しくアタッチされたレイヤーを指すように関数のハンドラーを更新する方法は次のとおりです。
Javaです。
RequestHandler実装:com.newrelic.java.HandlerWrapper::handleRequest。RequestStreamHandlerWrapper実装:com.newrelic.java.HandlerWrapper::handleStreamsRequest。
Python:
newrelic_lambda_wrapper.handler(アンダースコア)。ノードです。
- CommonJS:
newrelic-lambda-wrapper.handler(ハイフン)。 - ESM:
/opt/nodejs/node_modules/newrelic-esm-lambda-wrapper/index.handler(ハイフン)。
- CommonJS:
.Net の場合、ハンドラーを設定する必要はありません。
Go の場合、Lambda関数を計装するにはソースコードを変更する必要があることに注意してください。 設定変更だけでは十分ではありません。
輸送方法
各エージェント レイヤーには、CloudWatch をバイパスしてログとペイロードを New Relic に送信するための拡張機能も含まれています。 これにより、レイテンシとコストを削減できます。 ただし、関数のパフォーマンスと信頼性に影響を及ぼすリスクがあります。
New Relic Lambda レイヤーを追加すると、拡張機能が有効になり、ログ配布はデフォルトで無効になります。
New Relic で関数ログを表示する場合は、環境変数を使用して関数ログの拡張機能の送信を有効にする必要があります。
関数ログは、関数の呼び出し中に関数によって記録されたログにすぎないことに注意することが重要です。 拡張機能は、 START 、 END 、 REPORT行などの Lambda ランタイム ログを送信しません。
データを CloudWatch のみに送信するか、フォールバックとして送信するかを選択できます。詳細については、 CloudWatch フォールバックのドキュメントをご覧ください。