característica Disponibilidad
El control de flota para clúster de Kubernetes está generalmente disponible (GA). El soporte para la administración de agentes en hosts se encuentra actualmente en versión preliminar pública.
Para obtener una lista completa de agentes compatibles y sus entornos, consulte nuestra documentación de compatibilidad de tipos de agentes.
La función de vista previa pública se proporciona de conformidad con nuestras políticas de prelanzamiento.
El control de flota y su componente subyacente, Agente Control, están diseñados con seguridad de múltiples capas. Esta página proporciona una descripción general de las características de seguridad clave.
Importante: Protección de datos en reposo
Los secretos de Kubernetes solo están codificados en base64, lo que no es una forma de cifrado. Para proteger adecuadamente la información confidencial, como las claves privadas, es fundamental garantizar que el almacenamiento de datos etcd de su clúster de Kubernetes esté cifrado en reposo.
Conexiones seguras e integridad de la configuración
Para proteger los datos en tránsito y evitar la manipulación, control de flota emplea múltiples capas de seguridad para todas las comunicaciones.
Cifrado TLS: toda la comunicación entre el agente Control y el backend de New Relic, incluido el control de flota extremo, se transmite a través de canales seguros cifrados con TLS.
Firma criptográfica: además de TLS, todas las configuraciones entregadas desde el control de flota al agente Control están firmadas criptográficamente por New Relic. El agente Control verifica esta firma antes de aplicar cualquier configuración, garantizando que solo se ejecuten instrucciones auténticas y no modificadas en la entidad gestionada.
Autenticación y autorización
Control de Flota emplea mecanismos de autenticación distintos para sus diferentes componentes para garantizar un acceso seguro y apropiado.
Autenticación de control de agente: el componente Control de agente se autentica con el backend de control de flota empleando identidades a nivel de sistema, como un par de claves y token o un ID de cliente y un secreto. Esto garantiza que sólo las instancias autorizadas del agente Control puedan recibir instrucciones de administración.
Autenticación de agente: El agente individual desplegar mediante control de flota (como el agente de infraestructura u OTel recolector) se autentica con el extremo de ingesta de New Relic empleando su clave de licencia estándar New Relic.
Licencias de usuario: todas las acciones del usuario dentro de la UI y API de control de flota están regidas por el control de acceso basado en roles de New Relic. Para crear o gestionar flotas, el usuario necesita el rol de Administrador de la organización o un rol personalizado con licencias de administración de flotas equivalentes.
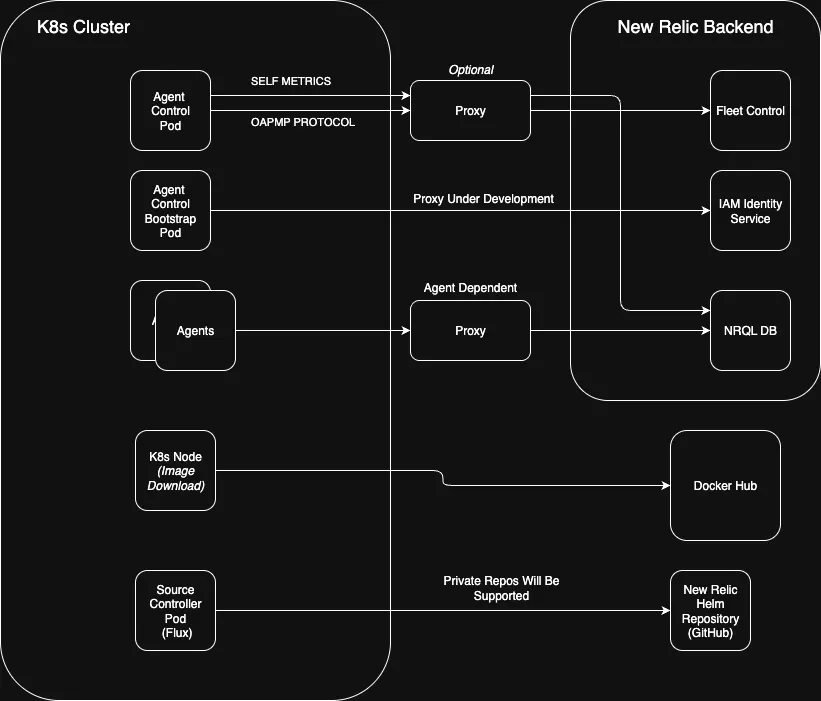
Soporte de proxy
Para entornos con salida de red restringida, Agente Control proporciona soporte completo para servidores proxy HTTP y HTTPS a nivel de sistema. Al configurar las variables de entorno estándar HTTP_PROXY y HTTPS_PROXY en sus hosts o dentro de su clúster de Kubernetes, toda la comunicación saliente del agente Control se enrutará de forma segura a través de su proxy especificado.
Acceso al repositorio público
Para simplificar la instalación y reducir la fricción de seguridad, todos los componentes necesarios para el control de flota están alojados en un repositorio público.
Gráficos Helm : Los gráficos Helm para instalar y gestionar el agente Control están alojados en un repositorio público New Relic en GitHub.
Imágenes de contenedor: Las imágenes de contenedor para el agente Control y su agente gestionado están alojadas en Docker Hub.